
Challenge - Writeups
Web
Akka University
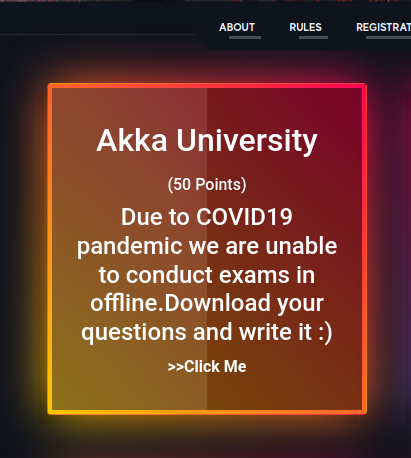
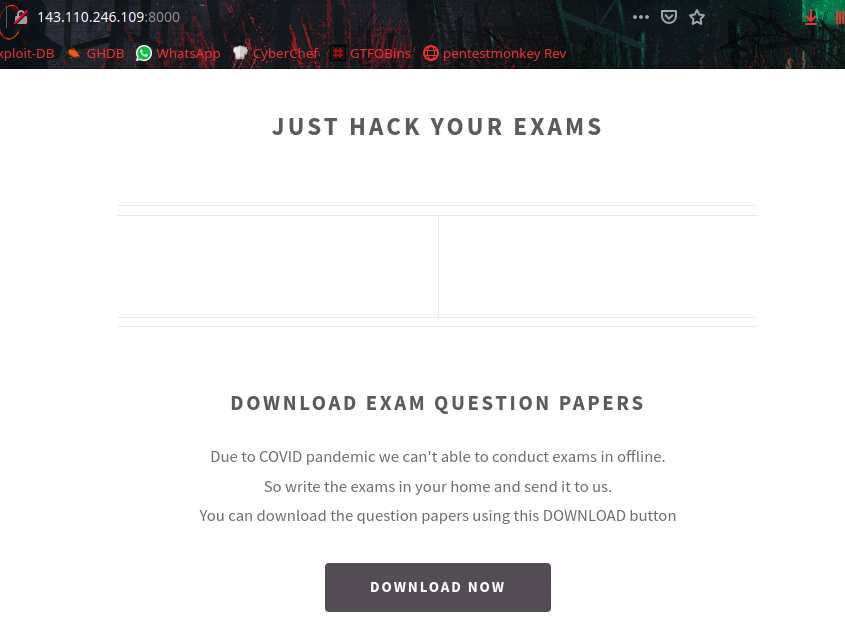
Going through webpage, there is a Download Now button to get Exam question papers,

When checking every picture they give,
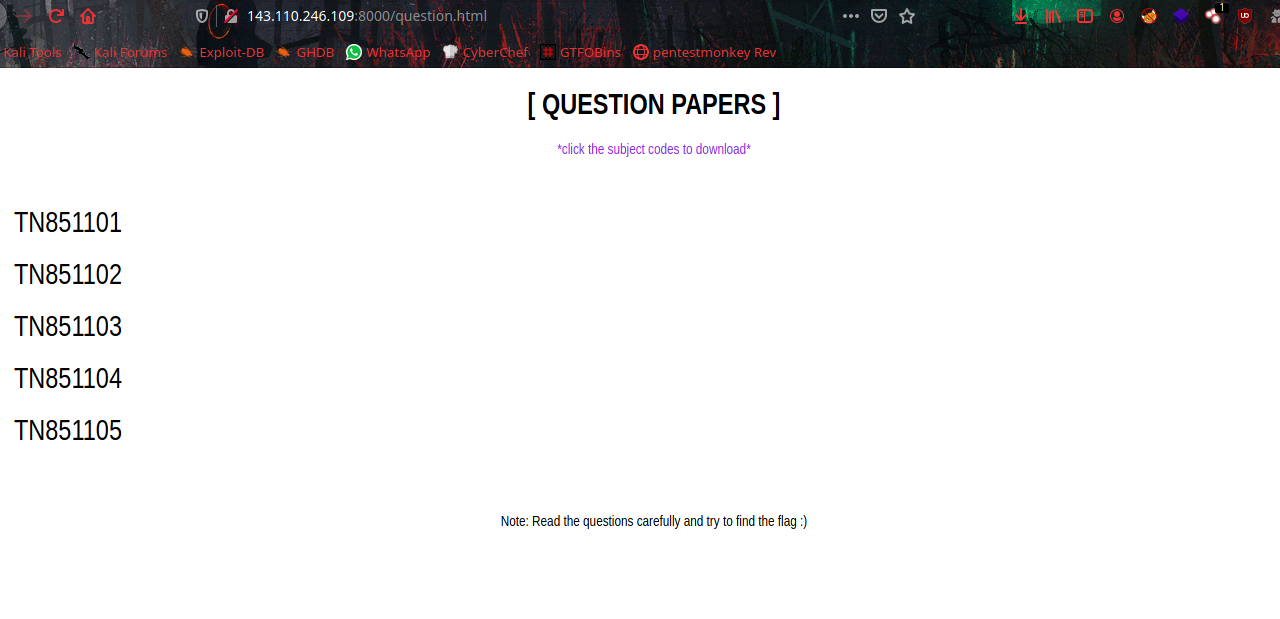
There is something interesting about url, The base64 encoded string of every question paper name displaying on url path to get the .png file
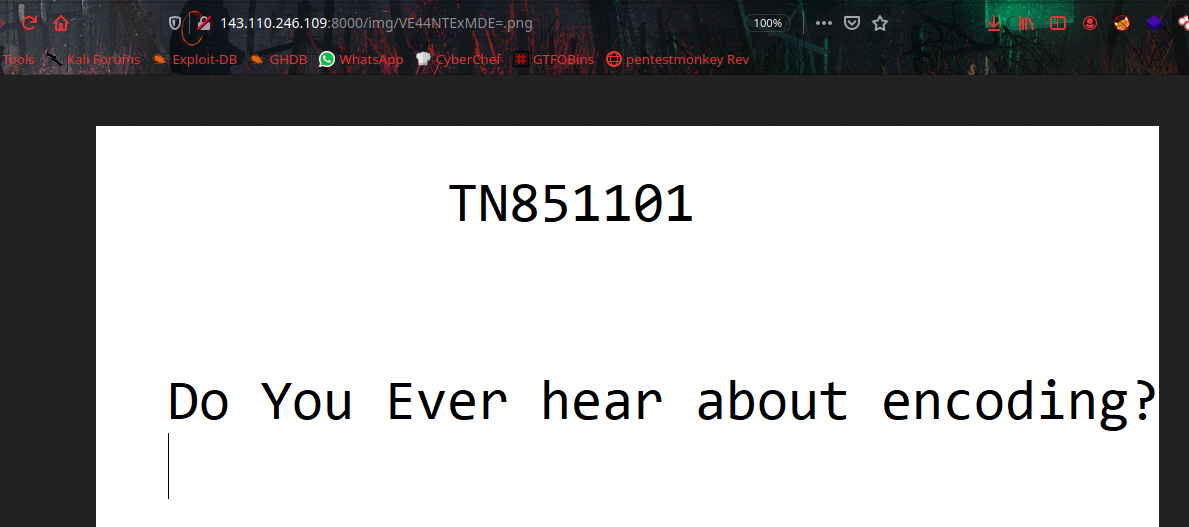
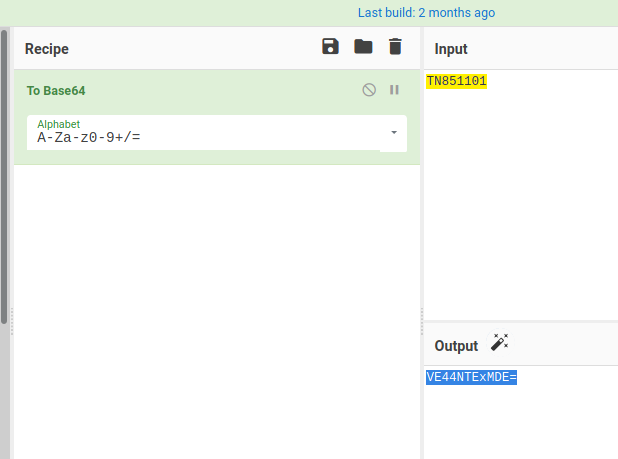
And the last Question paper doesn’t giving any Picture, So i encoded TN851105 string to base64 that is, VE44NTExMDU=
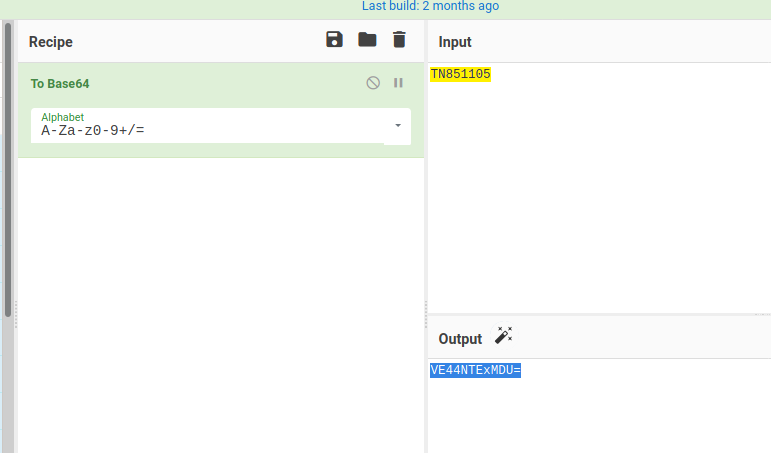
And put it in url path http://143.110.246.109:8000/img/VE44NTExMDU=.png they give the picture
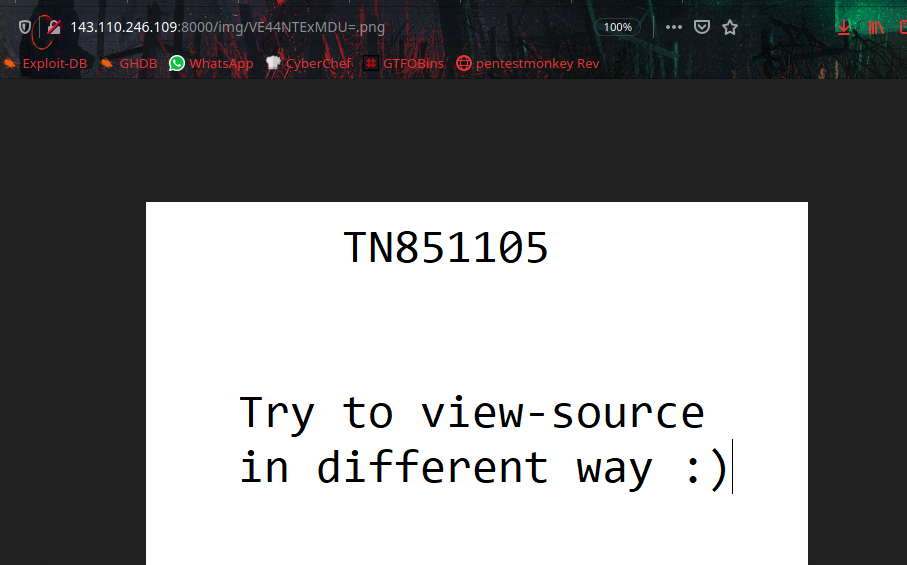
So they saying Try to view-source in different way, I paste the url on Chromium web browser, view-source:http://143.110.246.109:8000/img/VE44NTExMDU=.png
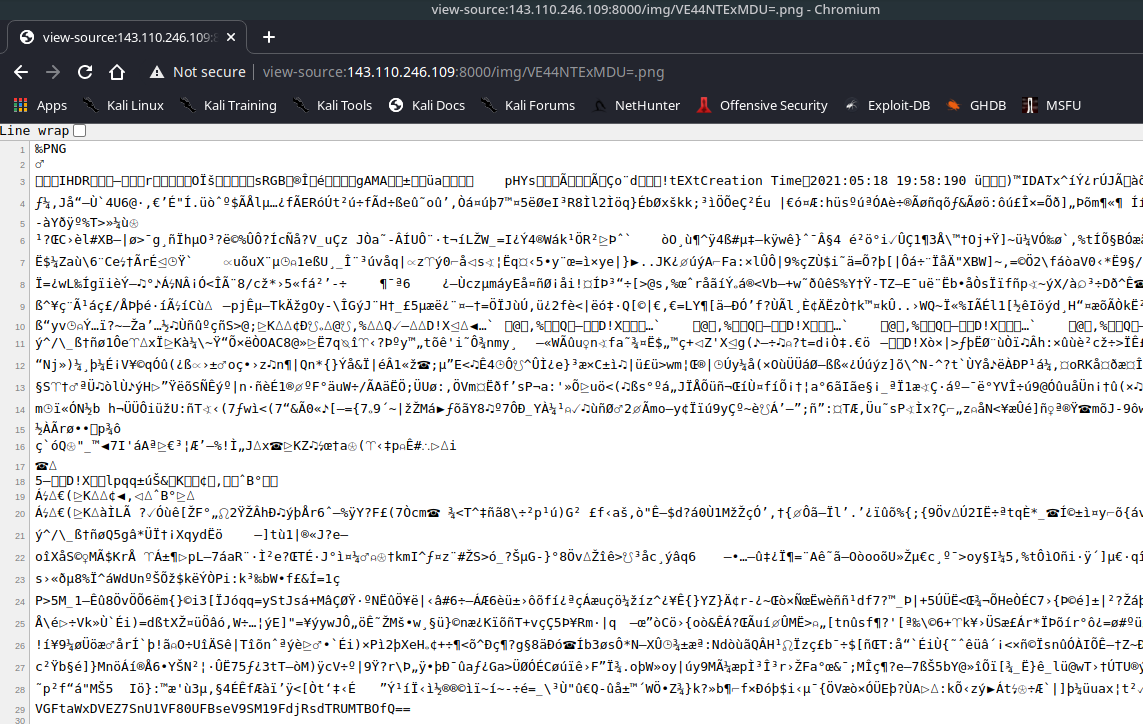
We can see there is base64 encoded string in the bottom, decode it to get the flag.
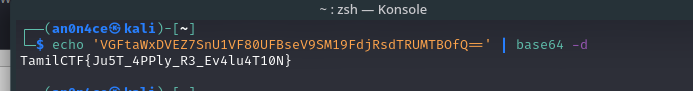
1
TamilCTF{Ju5T_4PPly_R3_Ev4lu4T10N}
CringeJS
When we looking in the webpage there is a login portal, we don’t have any credentials to login.
So i go for Forgot Password section and got an interesting JS file.
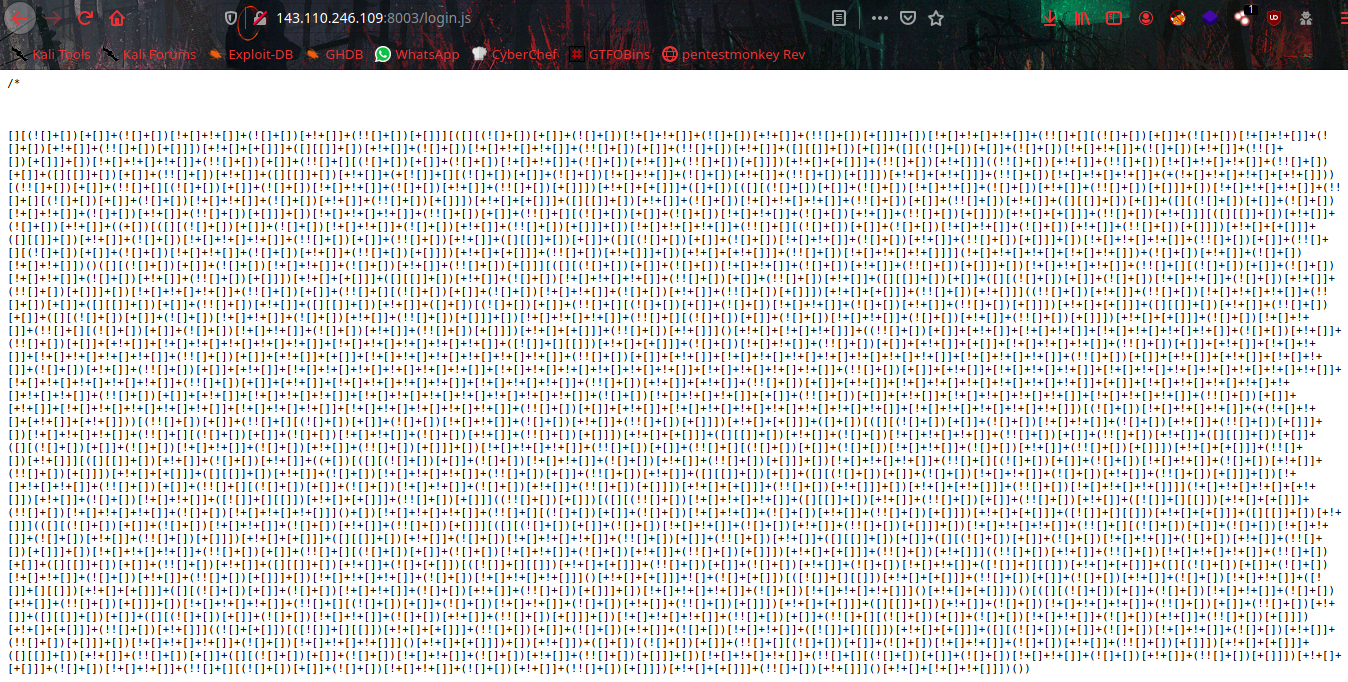
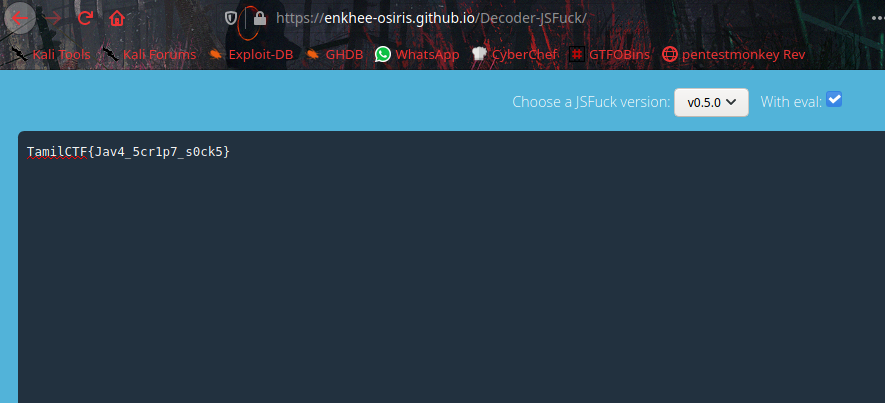
It’s JSFuck language, Decode it to get the flag.
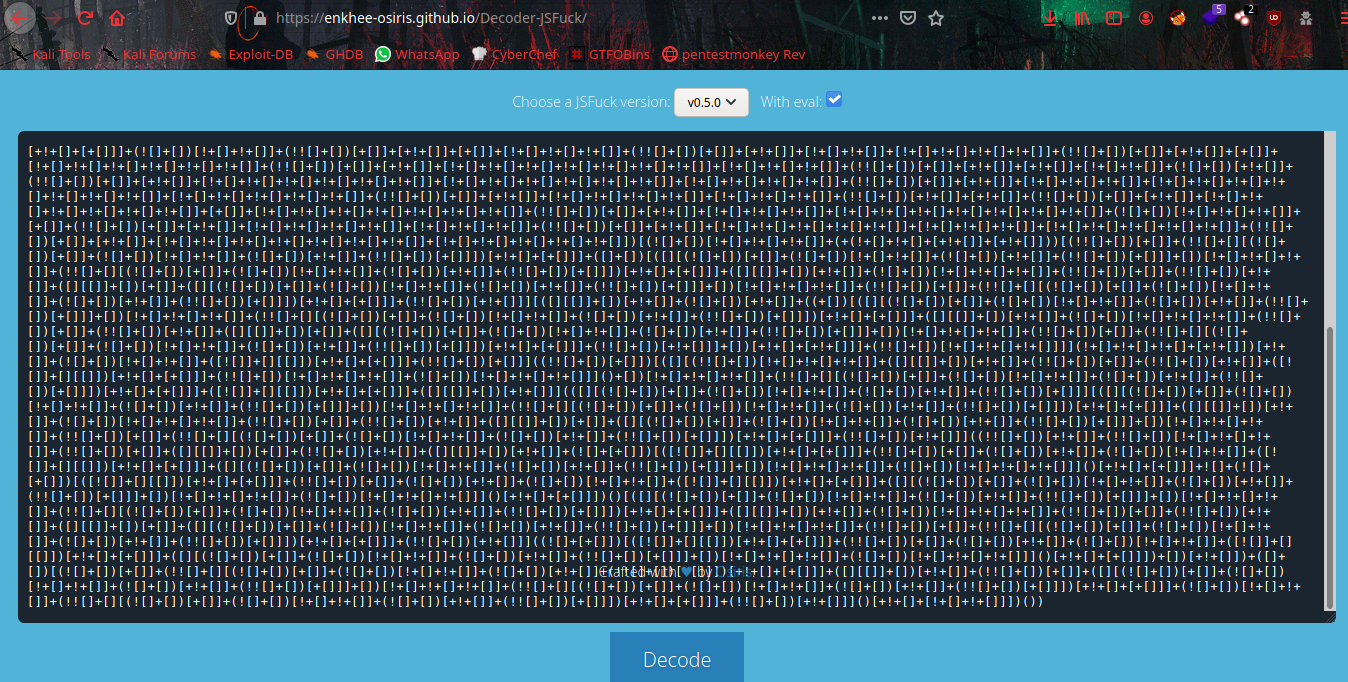
1
TamilCTF{Jav4_5cr1p7_s0ck5}
NotAPinterest
In the webpage we can download the 3 picture using the given link.
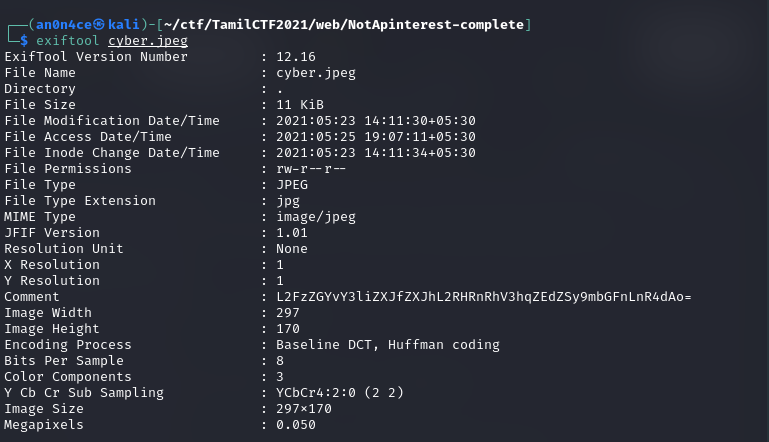
When we looking Exif-metadata of cyber.jpeg with exiftool.
We will get base64 encoded string, let’s decode it.
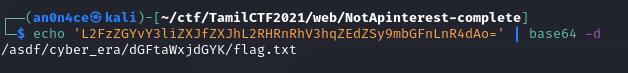
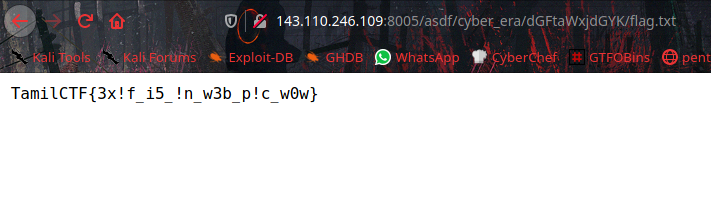
It’s a path to get flag.txt file, let’s open with browser.
1
TamilCTF{3x!f_i5_!n_w3b_p!c_w0w}
Delivery Boy
In the webpage we can see saying about a hint Can You Send A POST to Us?.
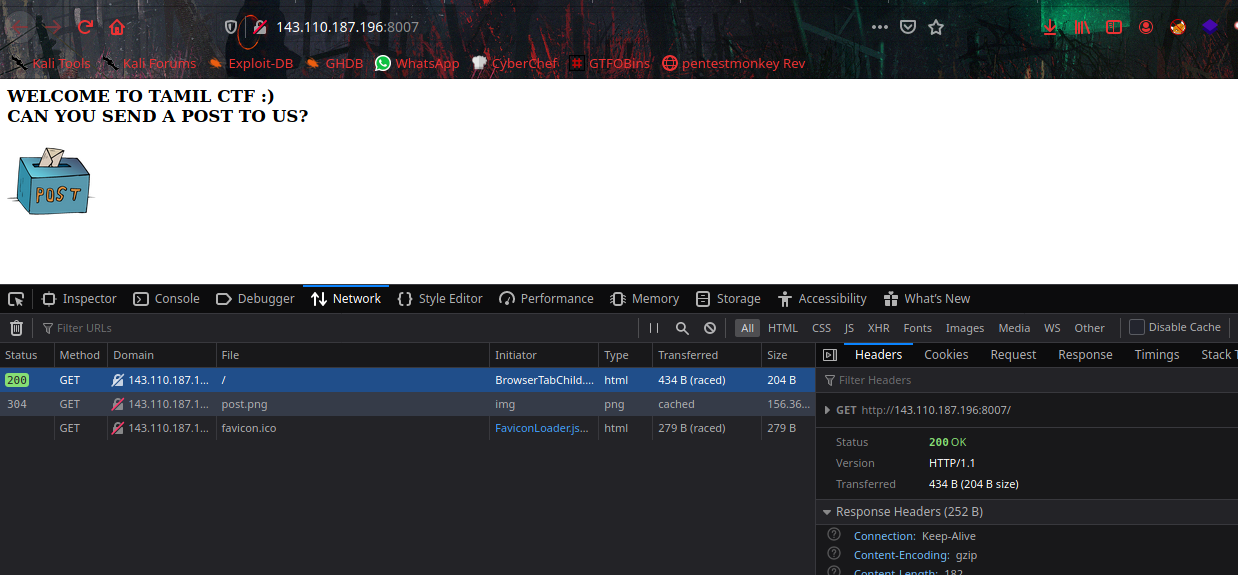
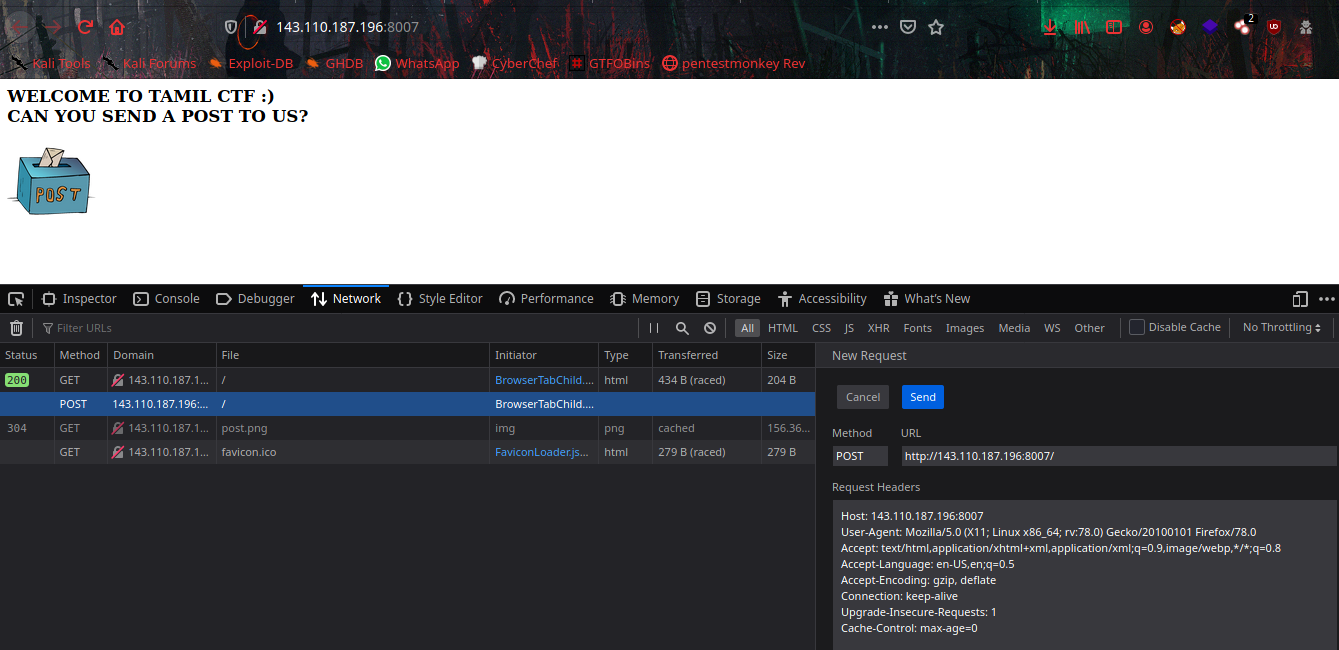
The request is GET method here, let’s edit the packet and send a POST request using browser Network Monitor.
In the Responce Tab we can get the flag.
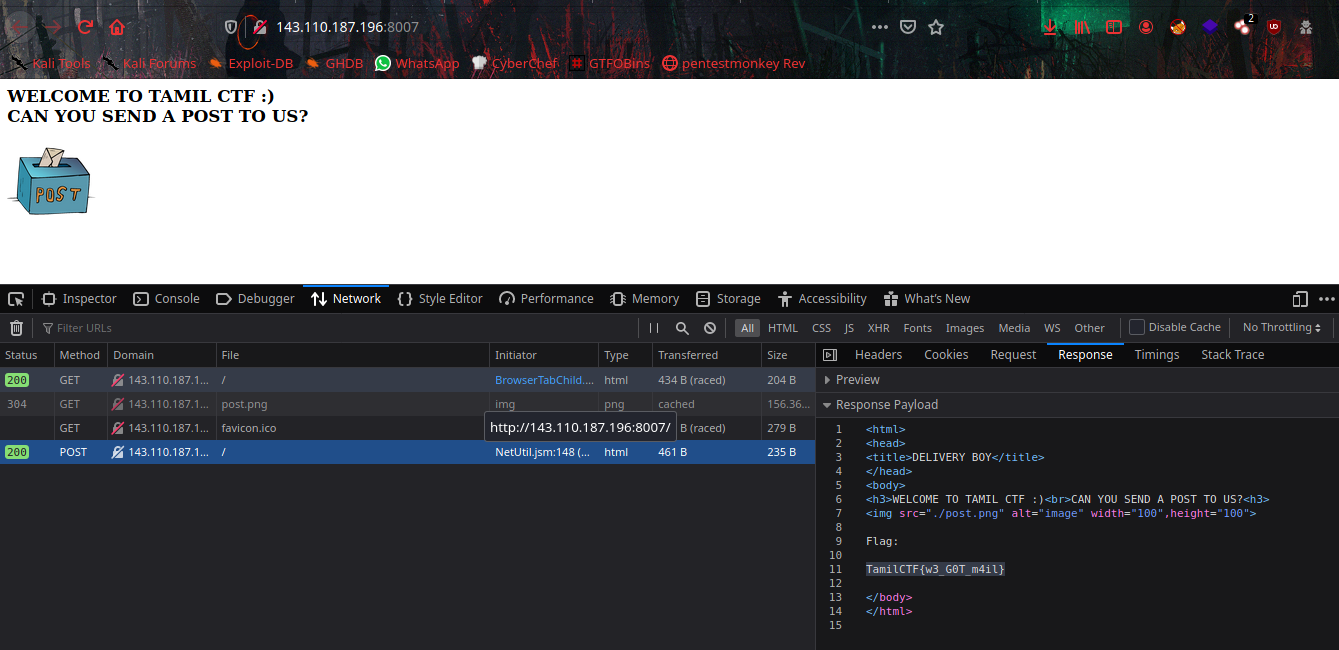
1
TamilCTF{w3_G0T_m4il}
Welcome Gem
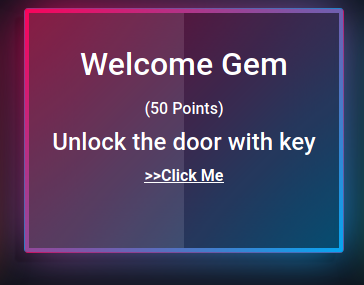
In the webpage we can see php source code.
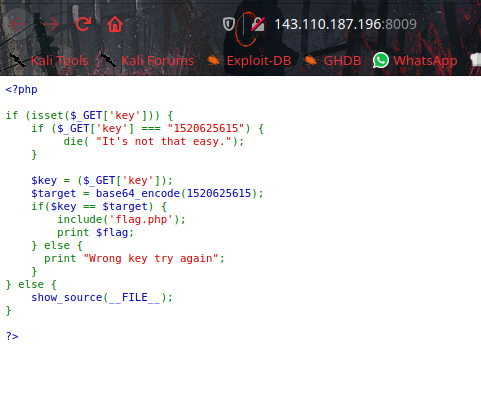
From this php code we can understand about key= parameter and that key will be base64 encoded string of 1520625615.
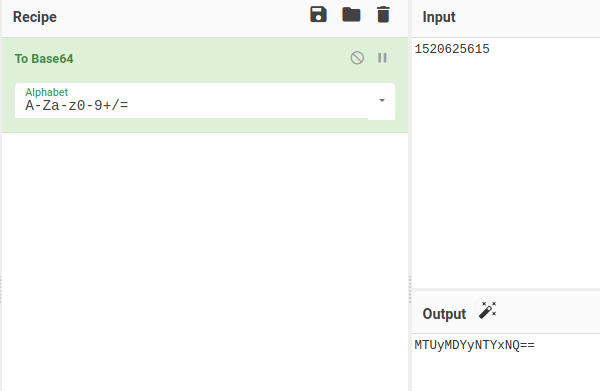
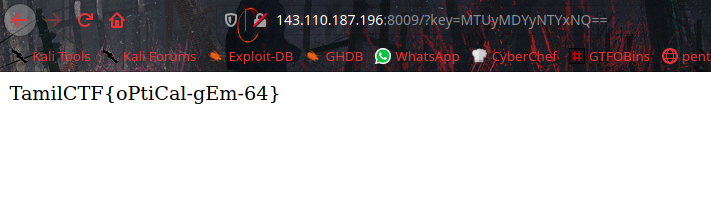
let’s open the browser and put the url http://143.110.187.196:8009/?key=MTUyMDYyNTYxNQ== to get the flag.
1
TamilCTF{oPtiCal-gEm-64}
Choco Cookies
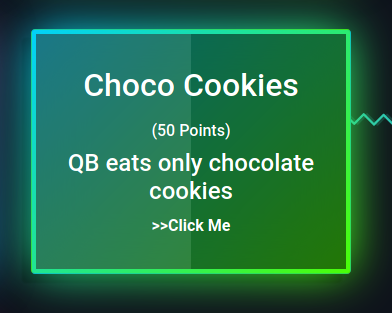
From the challenge name we know that it is something about Cookie: header.
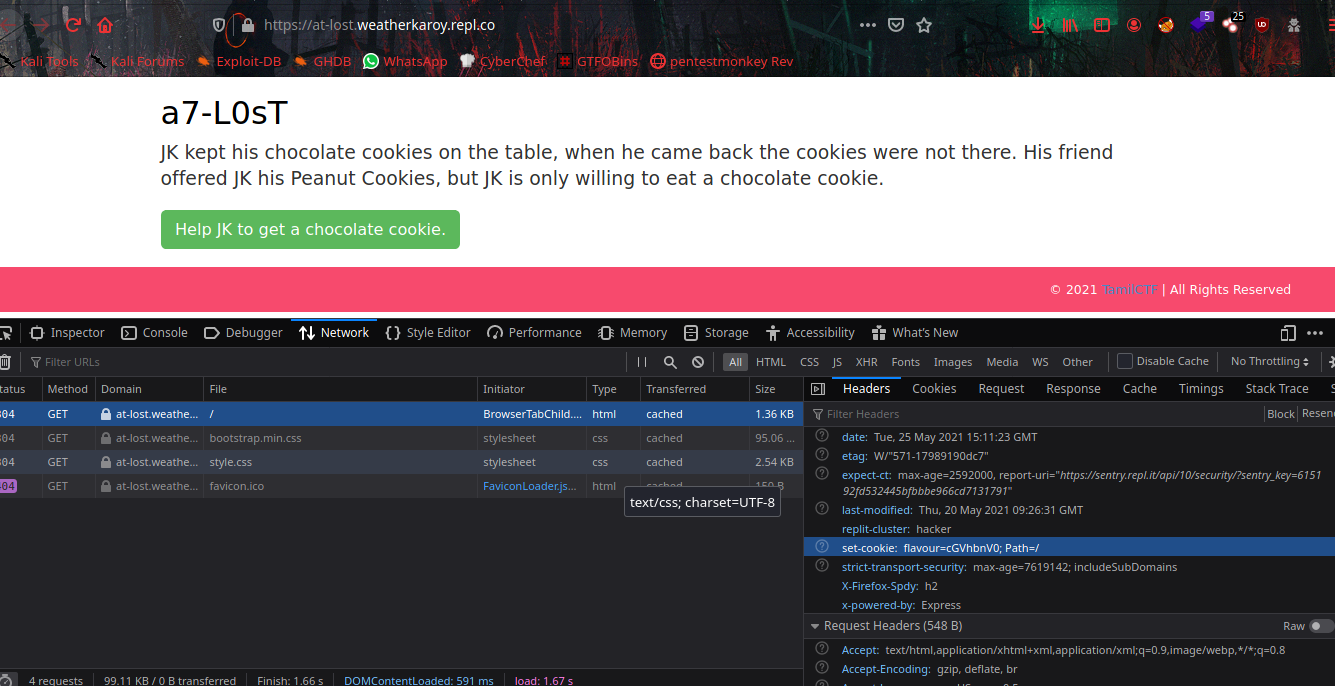
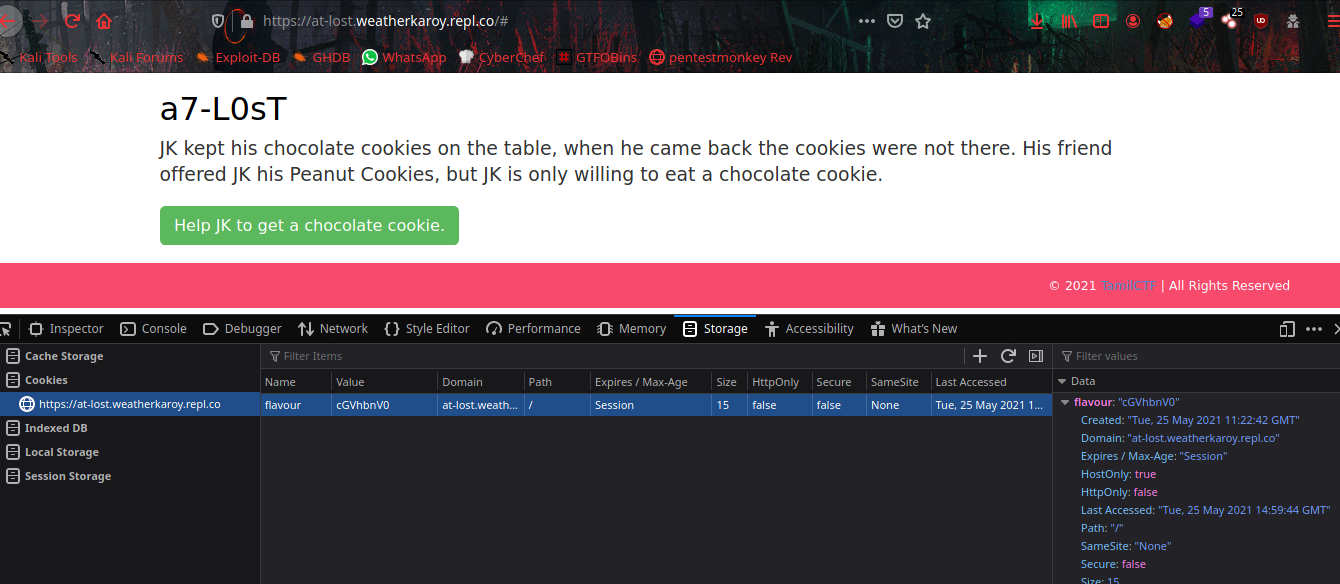
From the webpage there is base64 encoded cookie value is storing flavour as name.
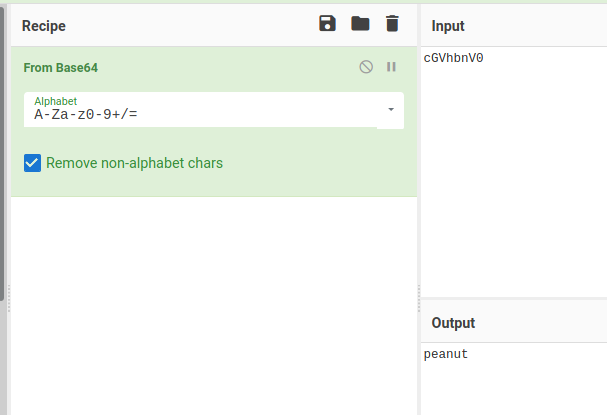
Once we decode it we get peanut.
From the Main webpage there is a hint JK is only willing to eat a chocolate cookie So let’s encode chocolate to base64.
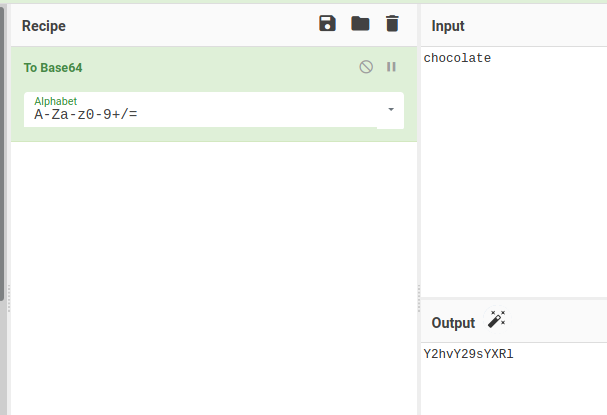
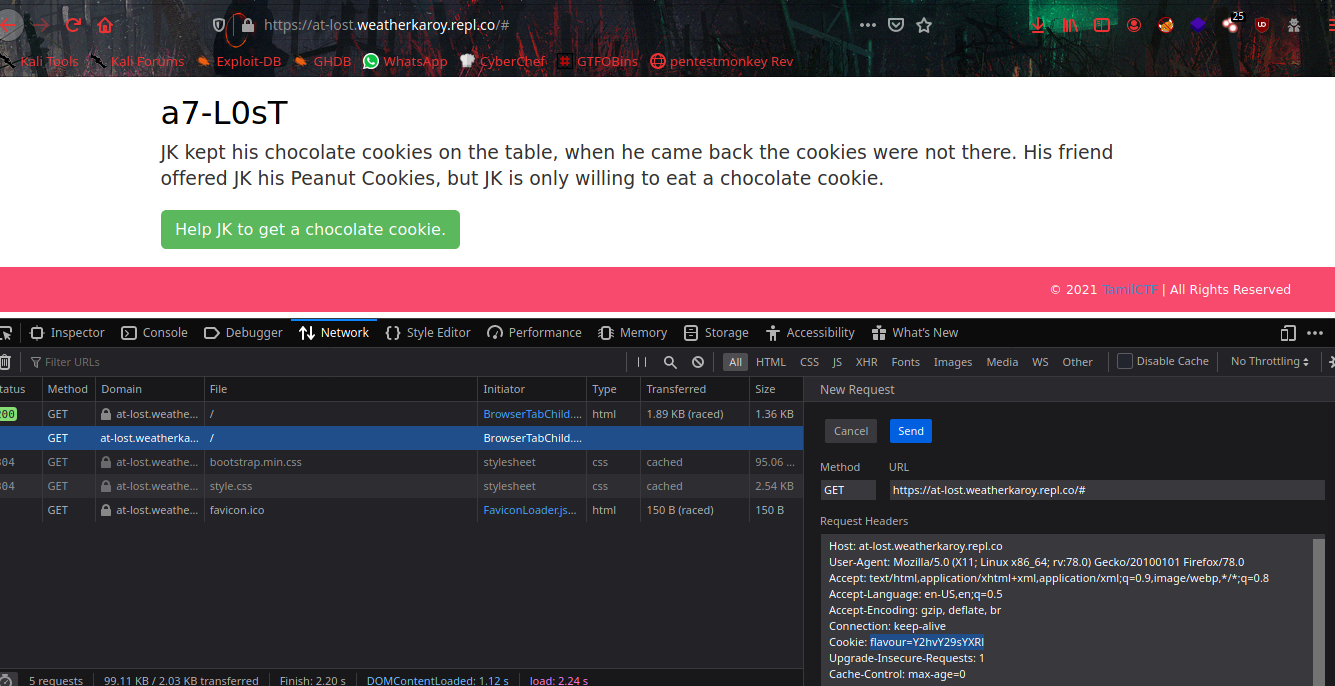
Then let’s edit the Cookie value to base64 encoded string of chocolate. Cookie: flavour=Y2hvY29sYXRl and resend the request.
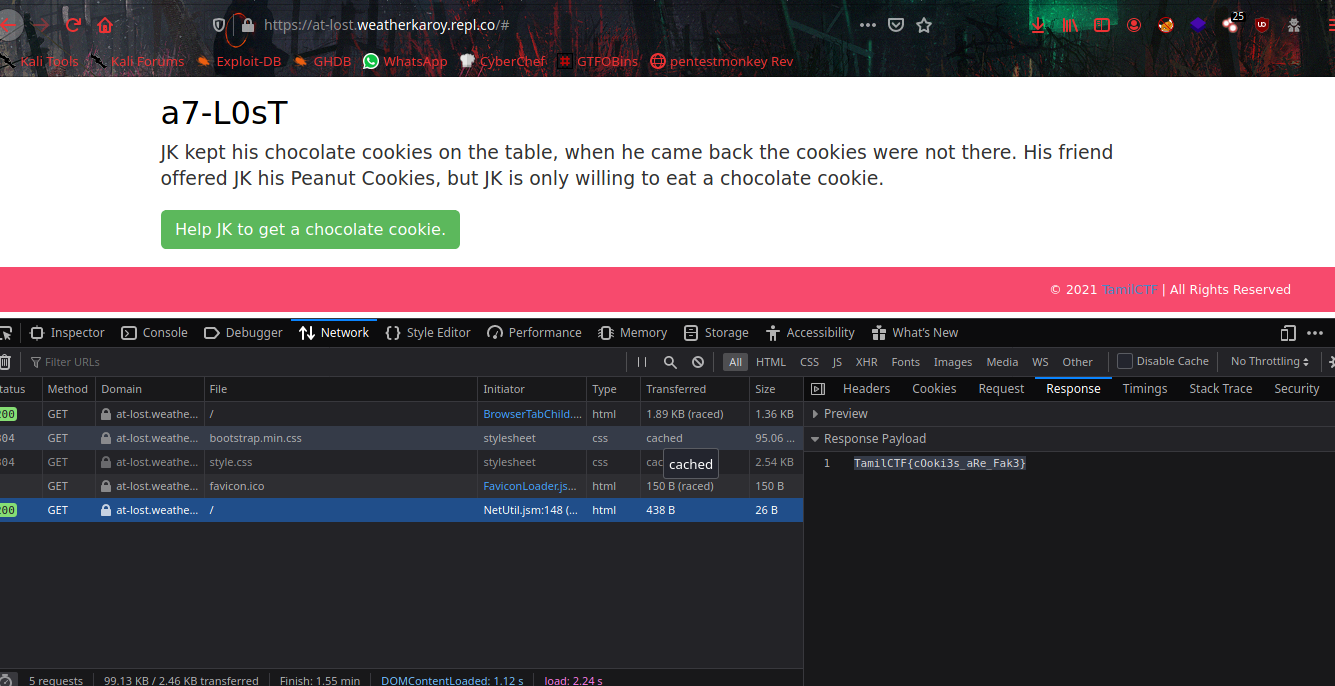
After this we can get the flag in the Responce Tab of Browser’s Network Monitor.
1
TamilCTF{cOoki3s_aRe_Fak3}
Cure Me

In the webpage there is a input column and cure button.
When put a term and Command, i.e med ;whoami. it gives current user name!
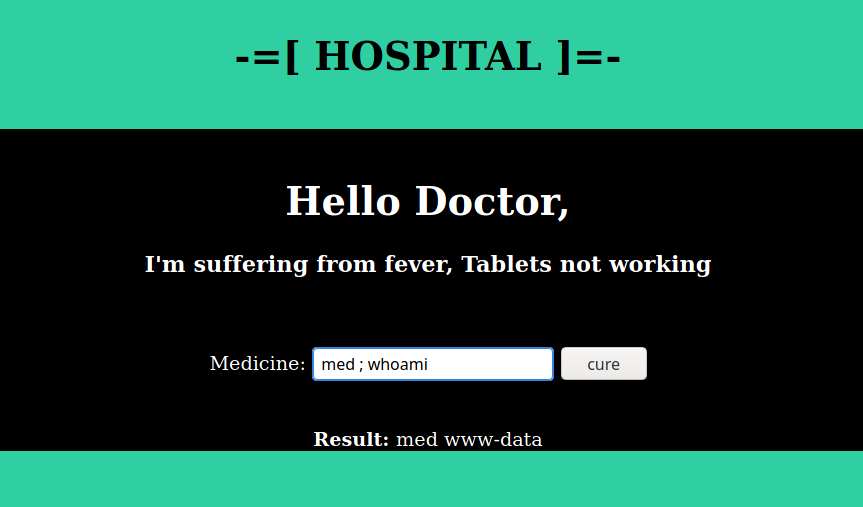
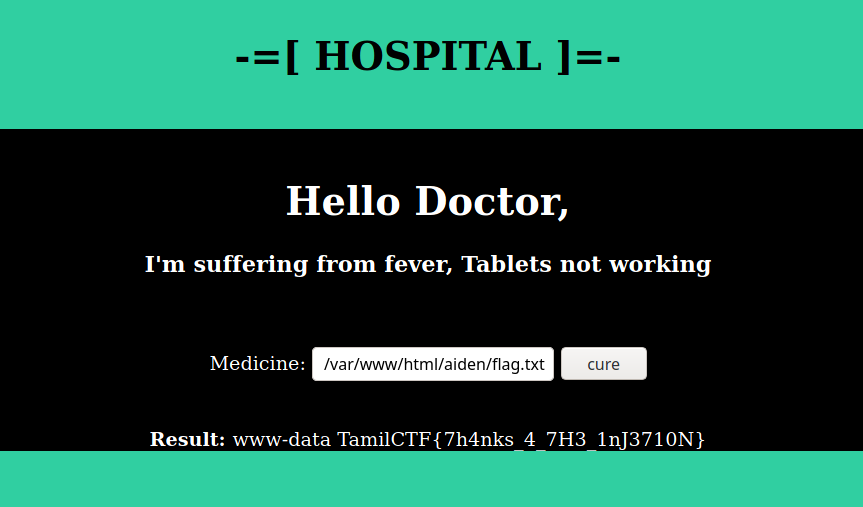
So the challenge has Command Injection vulnerability. looking further more Directories and files, we get flag.txt from /var/www/html/aiden/flag.txt
1
TamilCTF{7h4nks_4_7H3_1nJ3710N}
Forensic
GitHub
Here we get Zip Archived data of Github Repo.
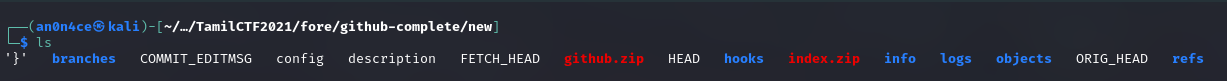
What i did here, i go through all directories and files, I came across flag has different parts. Actually it’s 4 part, first part of the flag will inside /logs/refs
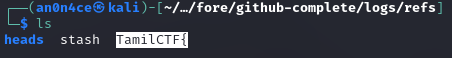
And 2nd part is on /logs/refs/heads/
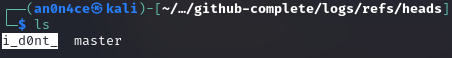
3rd part is on /branches
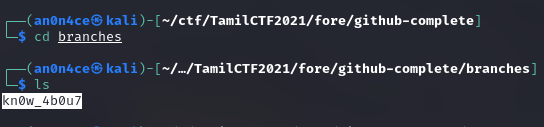
4th part is on index.zip file. It is password protected file, there is a config file you will get password from there.
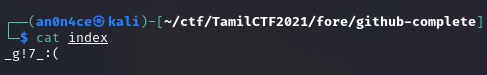
Finally get all part together to get the flag.
1
TamilCTF{i_d0nt_kn0w_4b0u7_g!7_:(}
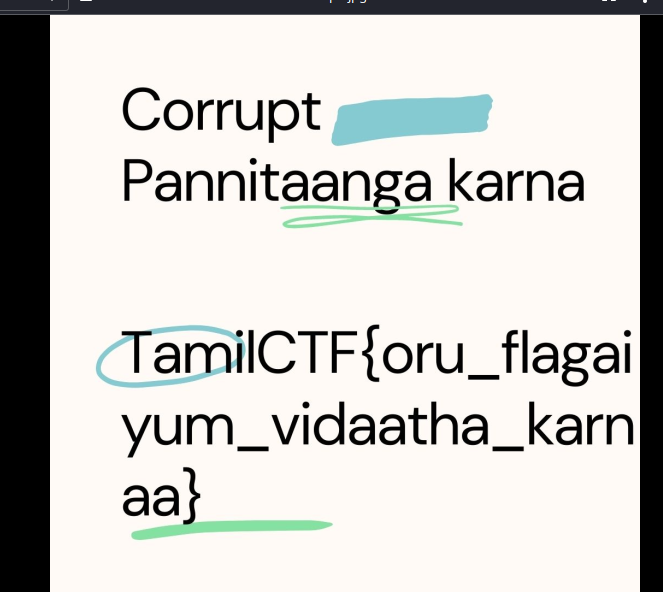
Corrupt Pannitaanga Karna
We will get a data file called cpk, when we looking the strings of the file it give its a JFIF file, a image file.
let’s check hex with hexeditor,
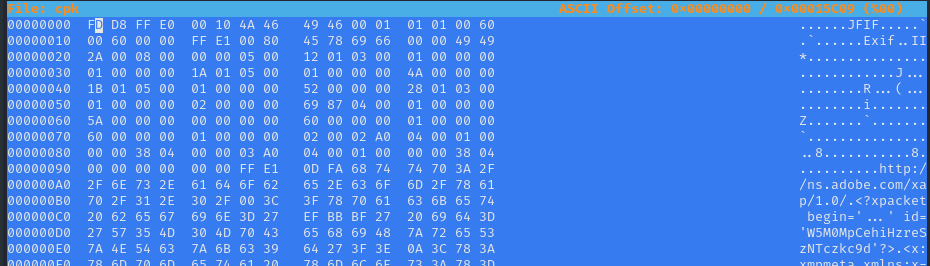
Magic header of file is wrong here, let’s correct it with right magic header of jpg FF D8 FF E0 00 and save and exit.
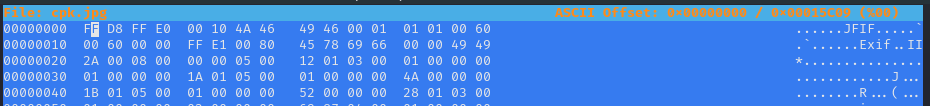
From the image we saved, we will get our flag.
1
TamilCTF{oru_flagaiyum_vidaatha_karnaa}
GoodBook
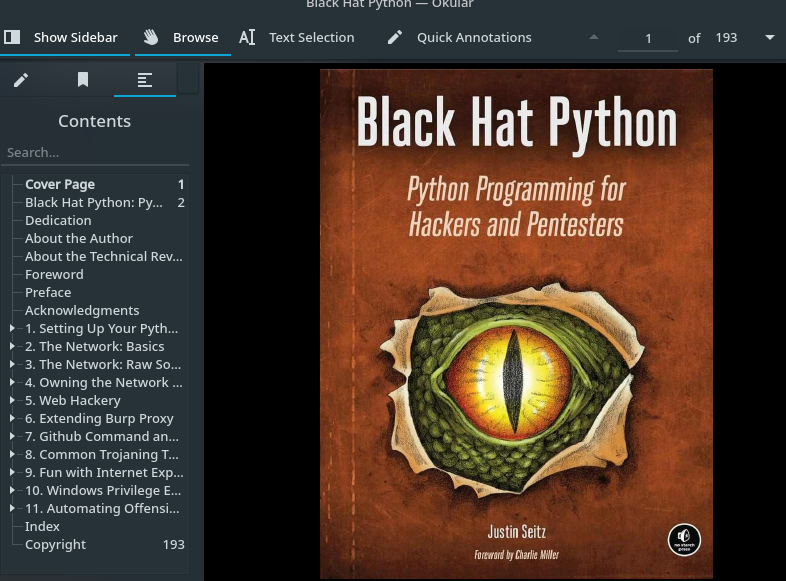
Here we get pdf file of book named Black Hat Python.
Nothing got from there, when we do binwalk, we get lots of file and at the bottom it has Zip Archived file.
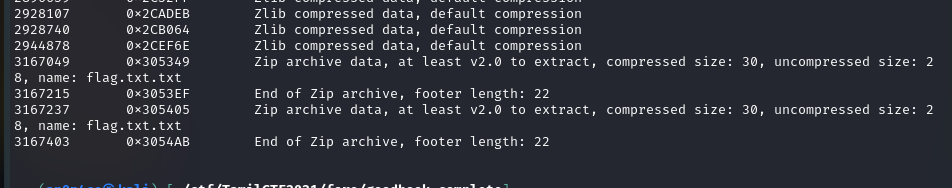
Let’s extract it with binwalk -e goodbook command. and list out the files
Extract the Zip Archived file to get flag.txt.
1
TamilCTF{3xtr4cti0n_is_n0n3}
Crypto
Boss Image
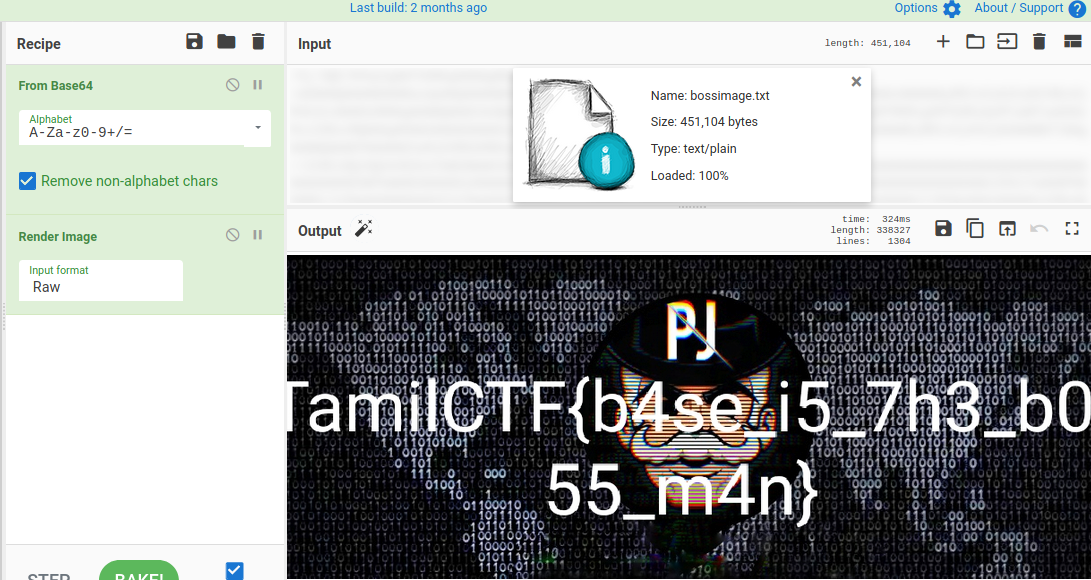
Here we get base64 encoded text file.
I used CyberChef. there is a file upload option, and decoded from base64
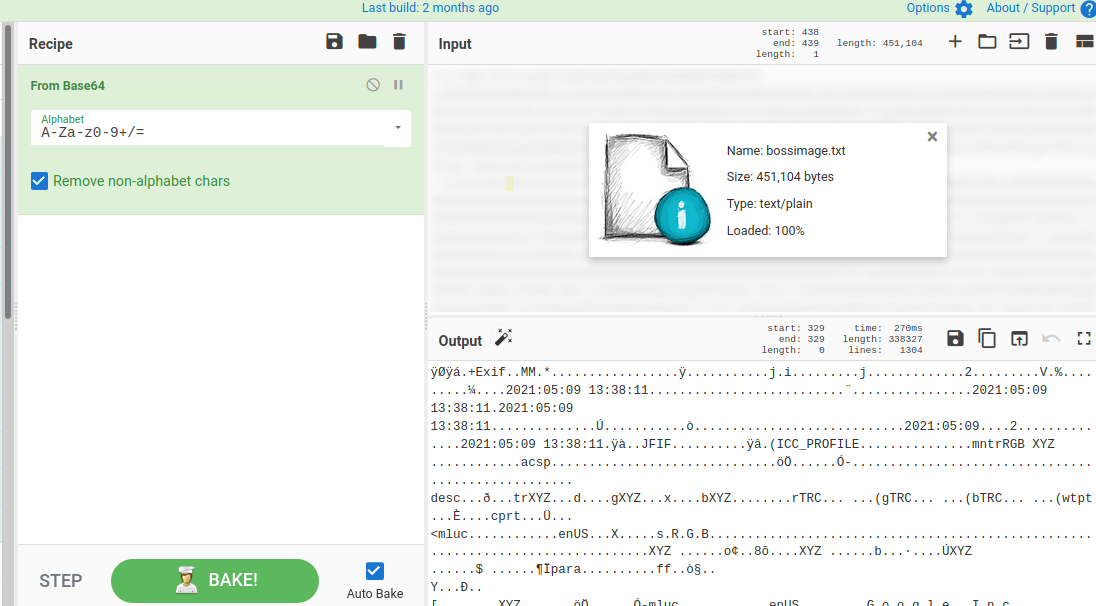
It seems a Image file, So i go for Render Image option on cyberchef. we will get the flag there.
1
TamilCTF{b4se_i5_7h3_b055_m4n}
FracMore
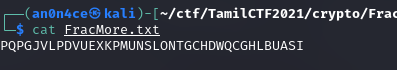
From the name of the challenge, we get its a Fractionated Morse Cipher.
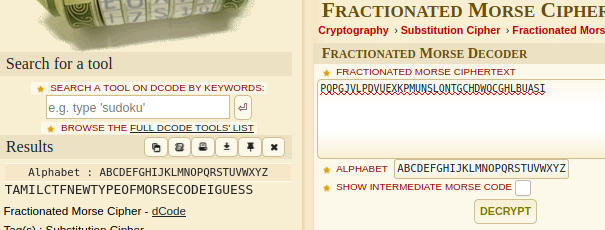
So decode to get the flag.
1
TamilCTF{NEWTYPEOFMORSECODEIGUESS}
Galaxy
It is Standard Galactic Alphabet.
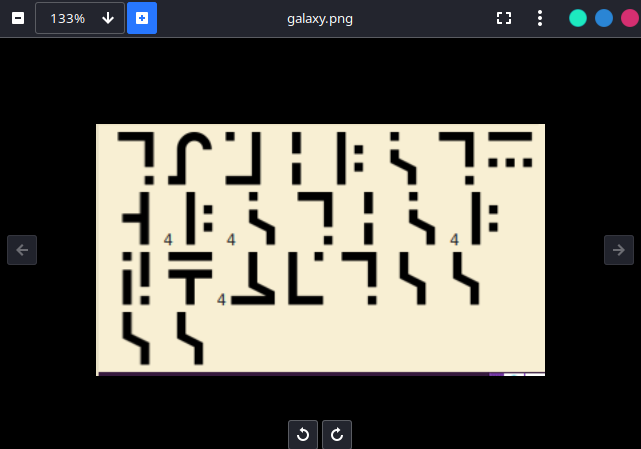
So decode it and follow the instructions of admin to get the flag.
1
TamilCTF{G4l4ctic_4lph4betssss!!}
RaaamSaAran
From the challenge name we know, it’s RSA decryption.
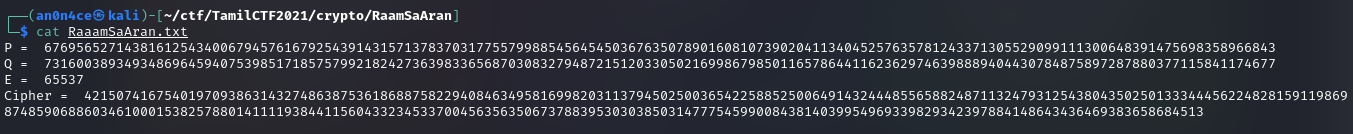
Here i used X-RSA tool to decrypt, and get the flag.
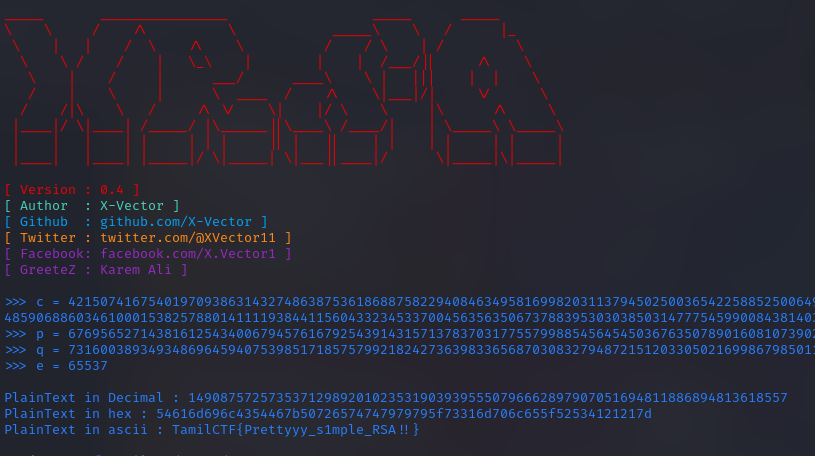
1
TamilCTF{Prettyyy_s1mple_RSA!!}
Stegno
UFO Signal
Here We get .wav file, open it with audacity and add spectrogram to get flag.
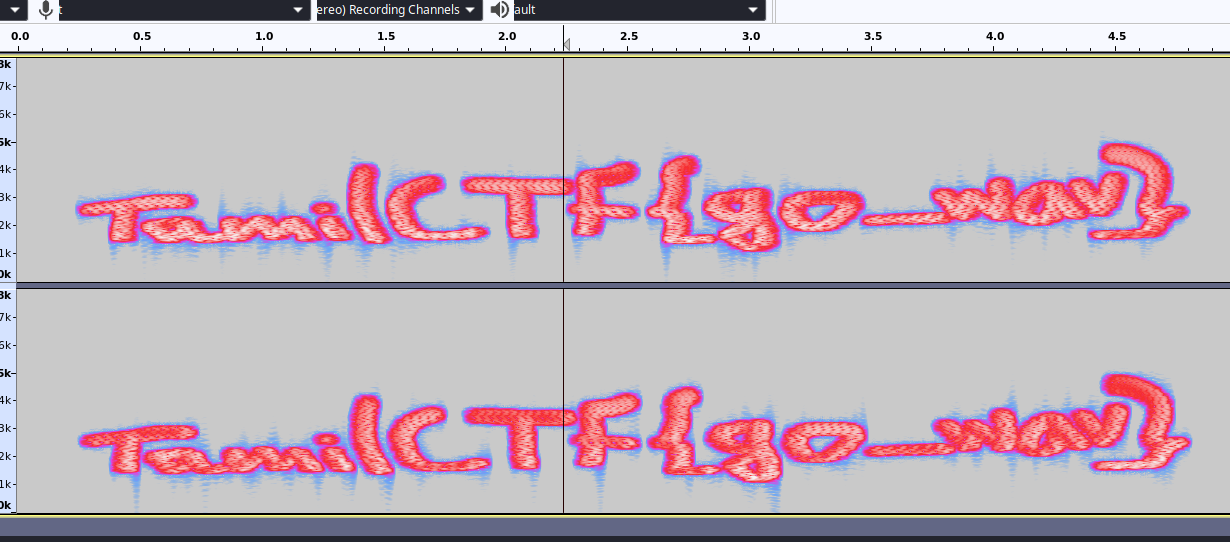
1
TamilCTF{go_wav}
OSINT
Who is this?
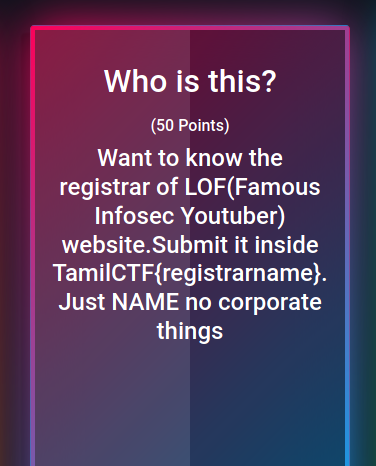
The challenge is to find the registrar name. The Youtuber is LiveOverFlow. To get the flag, run this command.
1
whois liveoverflow.com
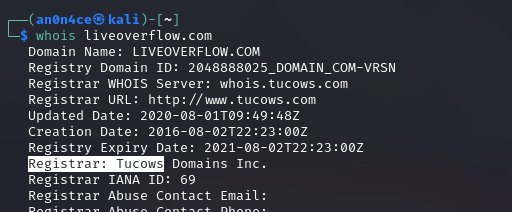
1
TamilCTF{tucows}
Photographer ah nanu?

We get an Image file here, I go for Google Image search.
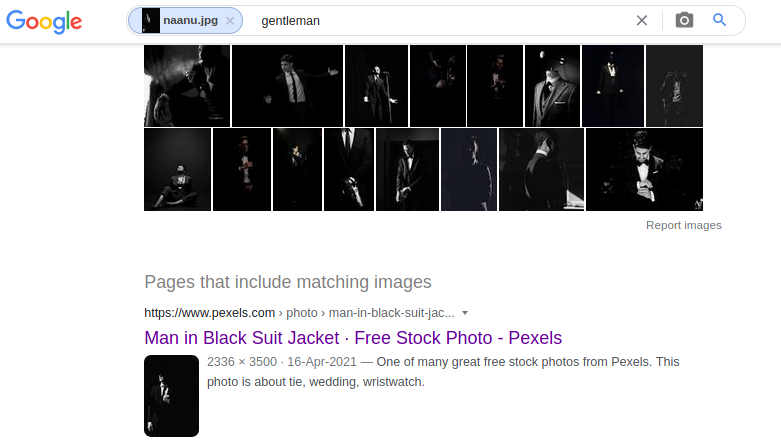
From the First Link We got the name of the Photographer. It is the flag.
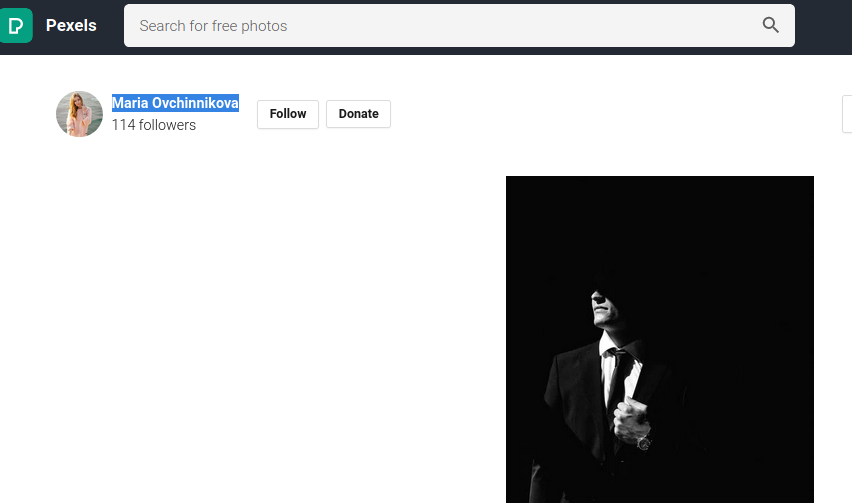
1
TamilCTF{Maria_Ovchinnikova}
