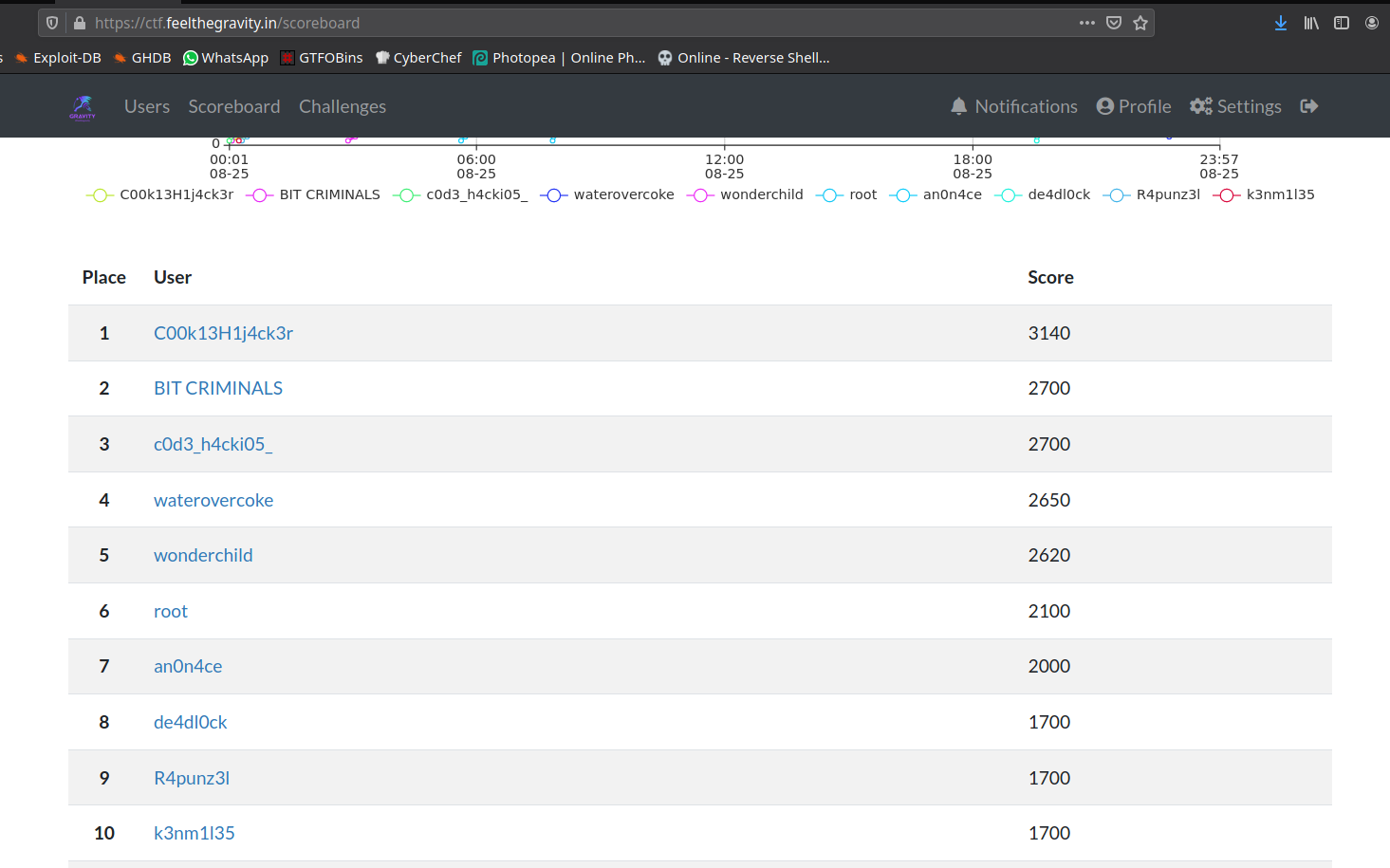
I secured 7th position in the 24 hour Gravithon CTF 2021 at the Indian Tech Fest.
Challenges-Writeups
Welcome
Warm Welcome
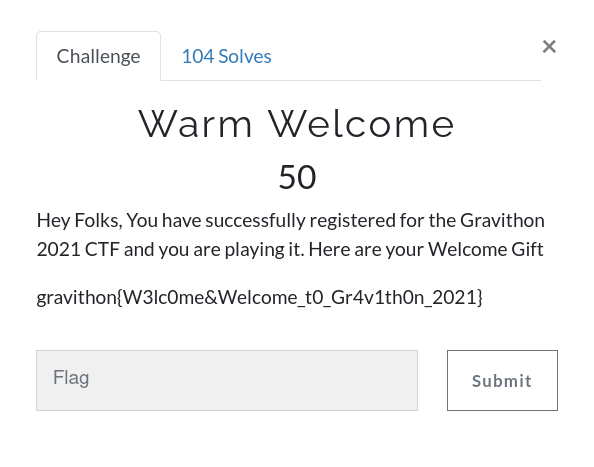
Flag is given there.
1
gravithon{W3lc0me&Welcome_t0_Gr4v1th0n_2021}
You Got it
You can find Hashtag on their Linkedin page.
1
gravithon{#feelthegravity}
How About Some Exploring the Things
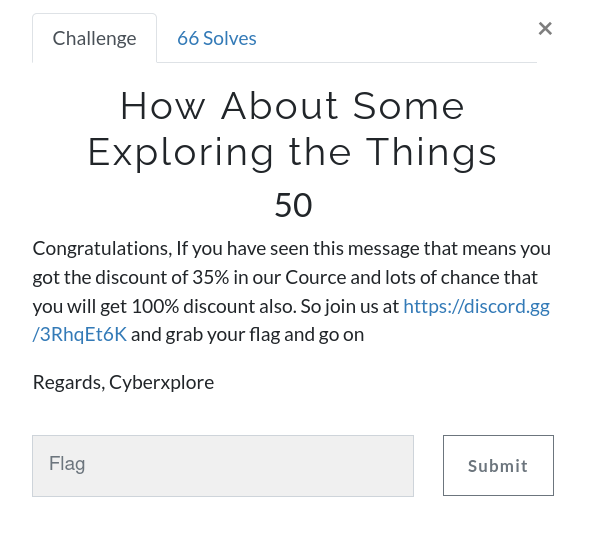
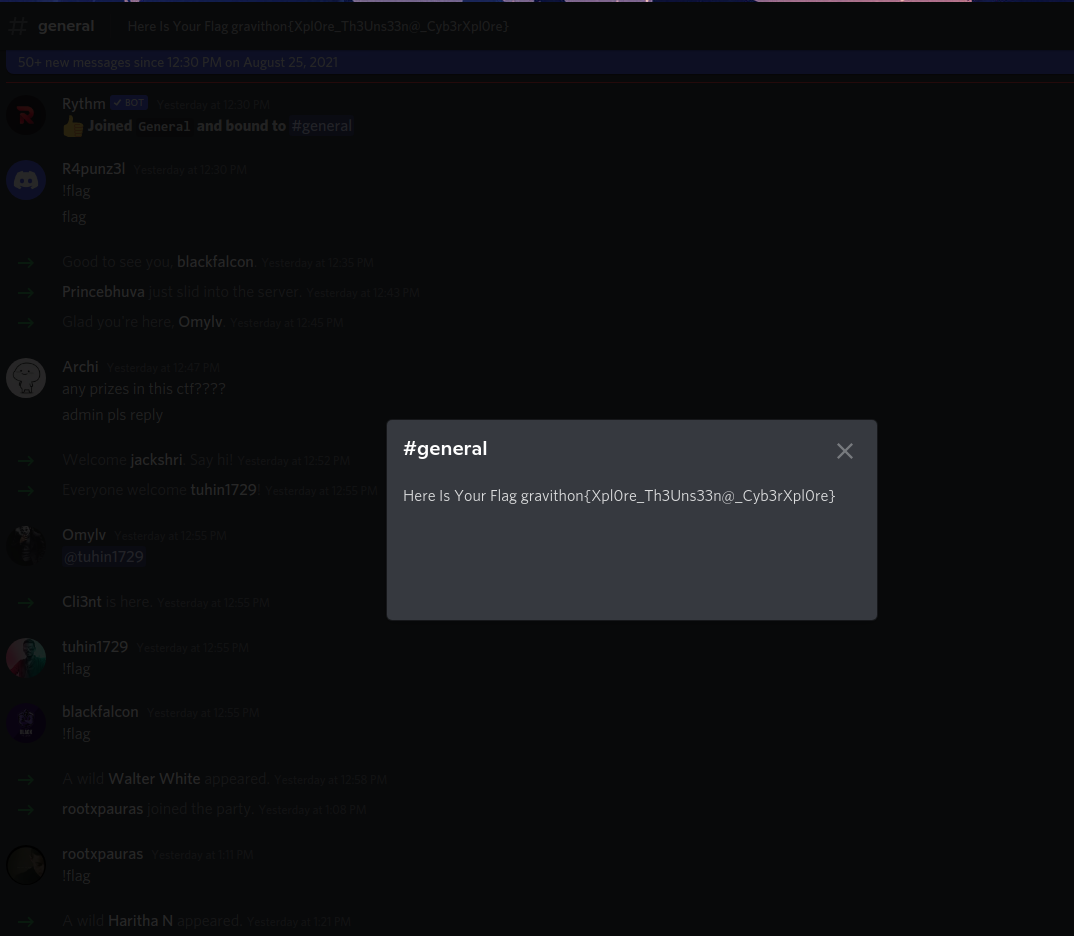
You can find flag on general chat in that discord server.
1
gravithon{Xpl0re_Th3Uns33n@_Cyb3rXpl0re}
ReadMe.md
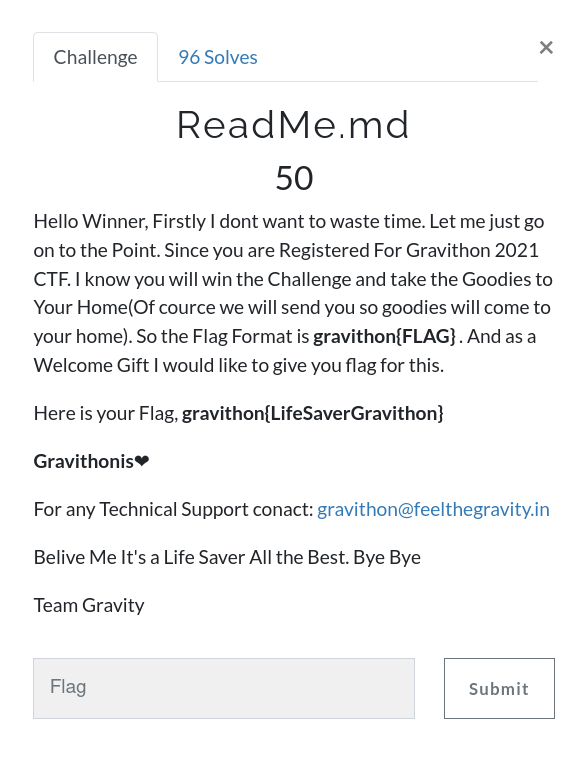
You can find flag on challenge description.
1
gravithon{LifeSaverGravithon}
Easy
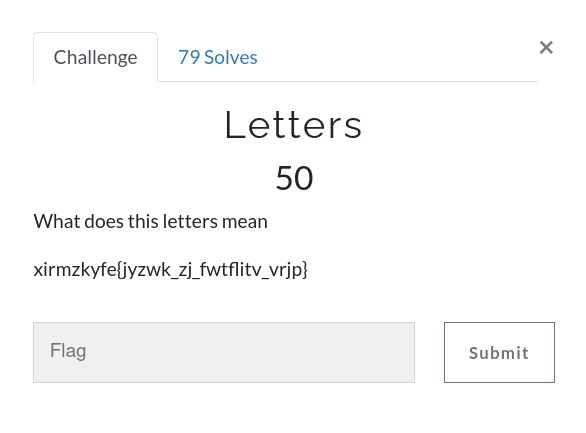
Letters
Challenge:
1
xirmzkyfe{jyzwk_zj_fwtflitv_vrjp}
It’s ROT9 cipher, We already know the flag format, when rotating the letters each letters rotates 9 times to get our flag format. that is g will assigned as x, Decode it and get the flag.
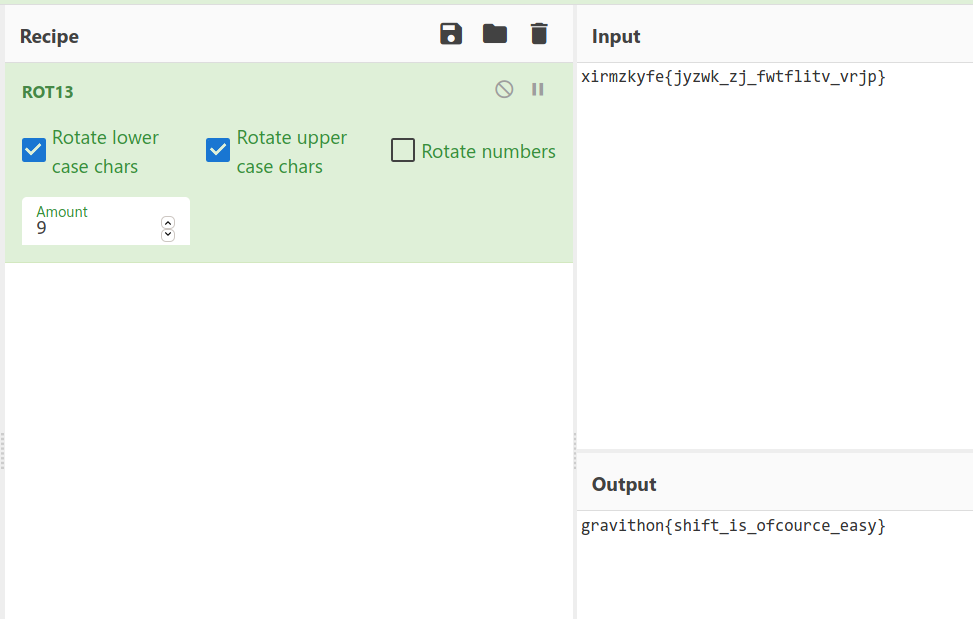
1
gravithon{shift_is_ofcource_easy}
Robbery
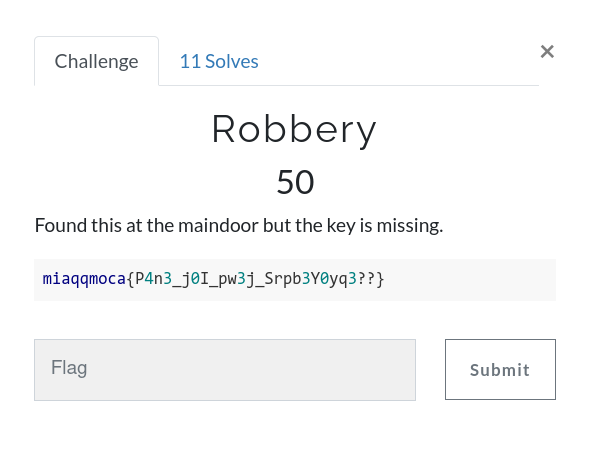
Challenge:
1
miaqqmoca{P4n3_j0I_pw3j_Srpb3Y0yq3??}
It’s Vigenère cipher, but key is missing, i guessed gravithon as key, it give right flag format, So need to find rest of the key. With the help of ReadMe.md challenge, you will get the key that is gravithonislove.
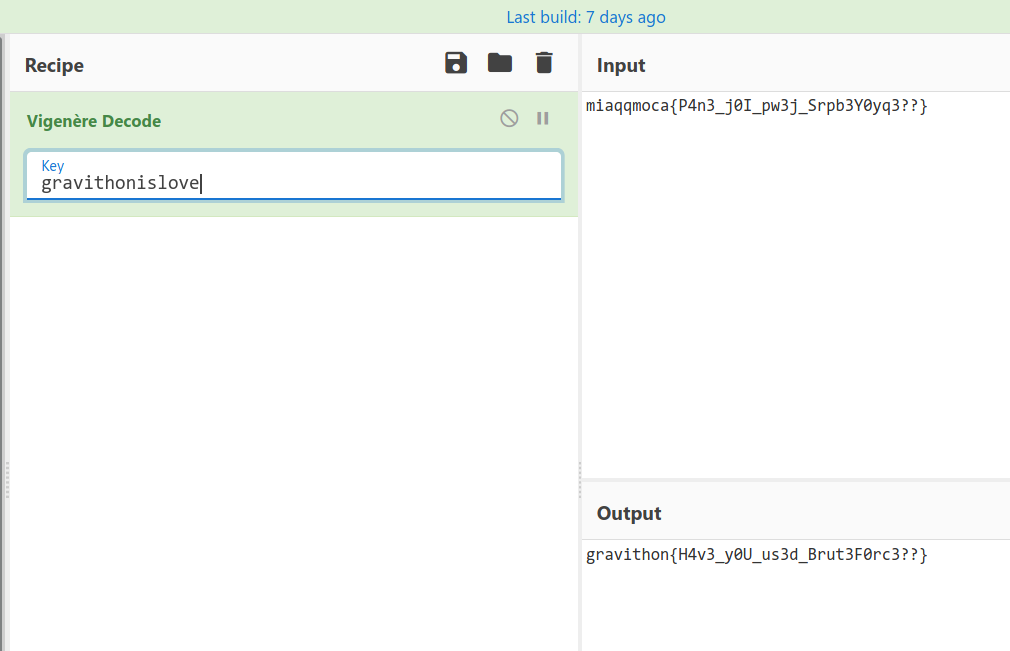
1
gravithon{H4v3_y0U_us3d_Brut3F0rc3??}
TIK TOK
Challenge:
1
-- ----- .-. ... ...-- .. ... ....- .-.. .-- .- -.-- ... -... ...-- . ... -
It’s a Morse Code. Decode to get your flag.
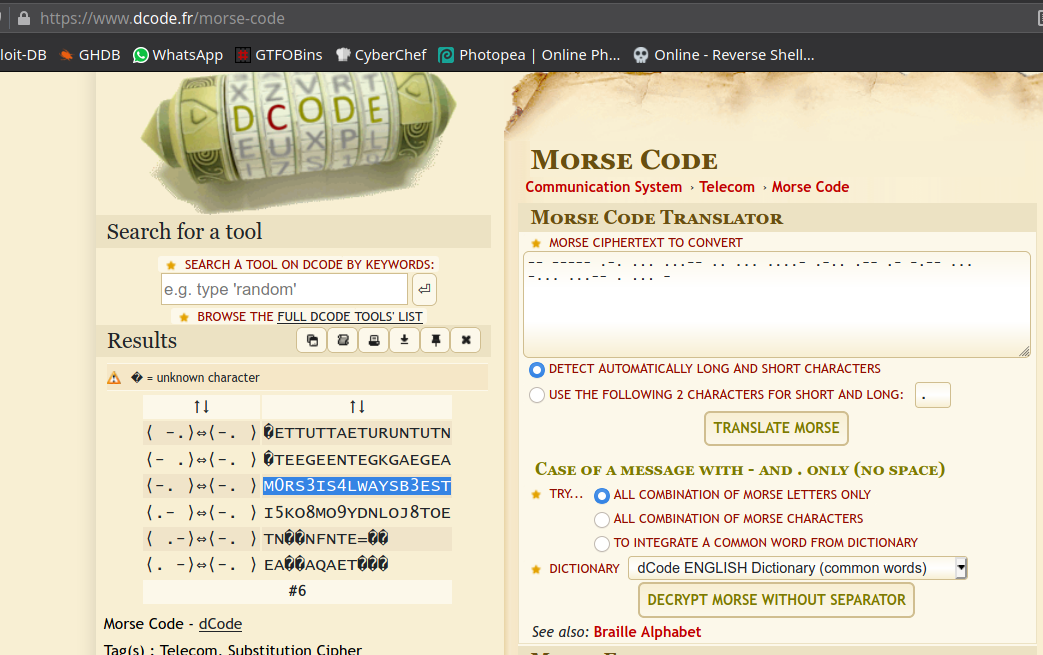
1
gravithon{M0RS3IS4LWAYSB3EST}
Binary always Awsome
Challenge:
1
000000000000000000000000000000110010000010000000000010000000000000000000000010000000000000000000000000000000011011011011001111010010010000000000000000000000000000000000000000000100010000000000000100011011000000000000000000000000000000000000000000000000000000000000000100010010000000000000000000000000000000000100011011100010000000000000000000000000000000000100001001001001001001001001001001001001001001001100010001100011011001001001100010010001001001001001001001001001001001100000000000000000000000000000000000100011011000000000000100010010001001001001001100100011011001001001100010010000100001001001001001001001100001001001001001001001001100011000000000100010000000000000000000000000000000000000000000000000000000000000000000100011000000000000000000000000000000000000000000000000100000000000000000000000000100010001001100
It’s a Binary Fuck Language. Decode to get your flag.
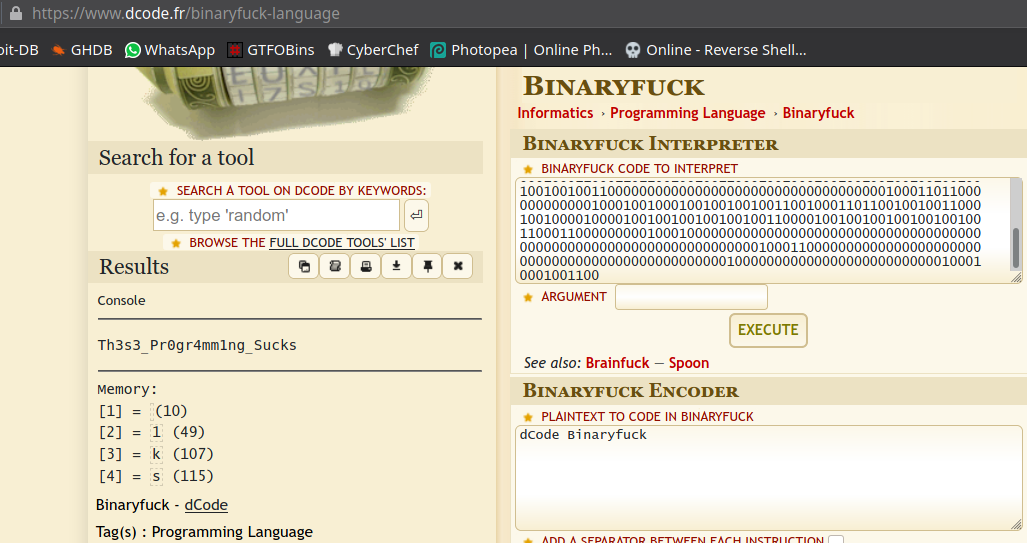
1
gravithon{Th3s3_Pr0gr4mm1ng_Sucks}
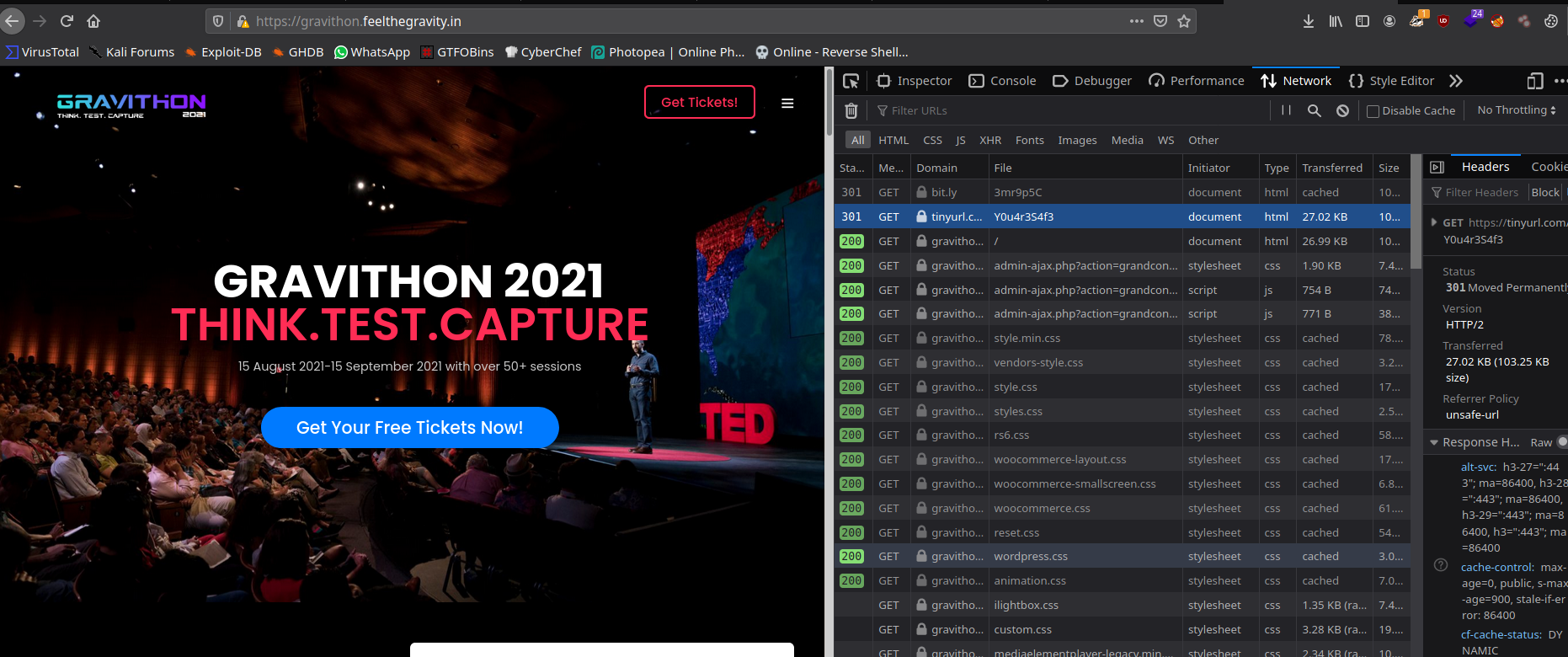
Everything is Not Visible
Here the given link was https://bit.ly/3mr9p5C , With help of Browser’s Network Monitor Tab, you can see the all contents that loading, and it is double shorted URL, that is bit.ly and tinyurl from the name of that url we get our flag.
1
gravithon{Y0u4r3S4f3}
So Loudd
Challenge: morse.wav
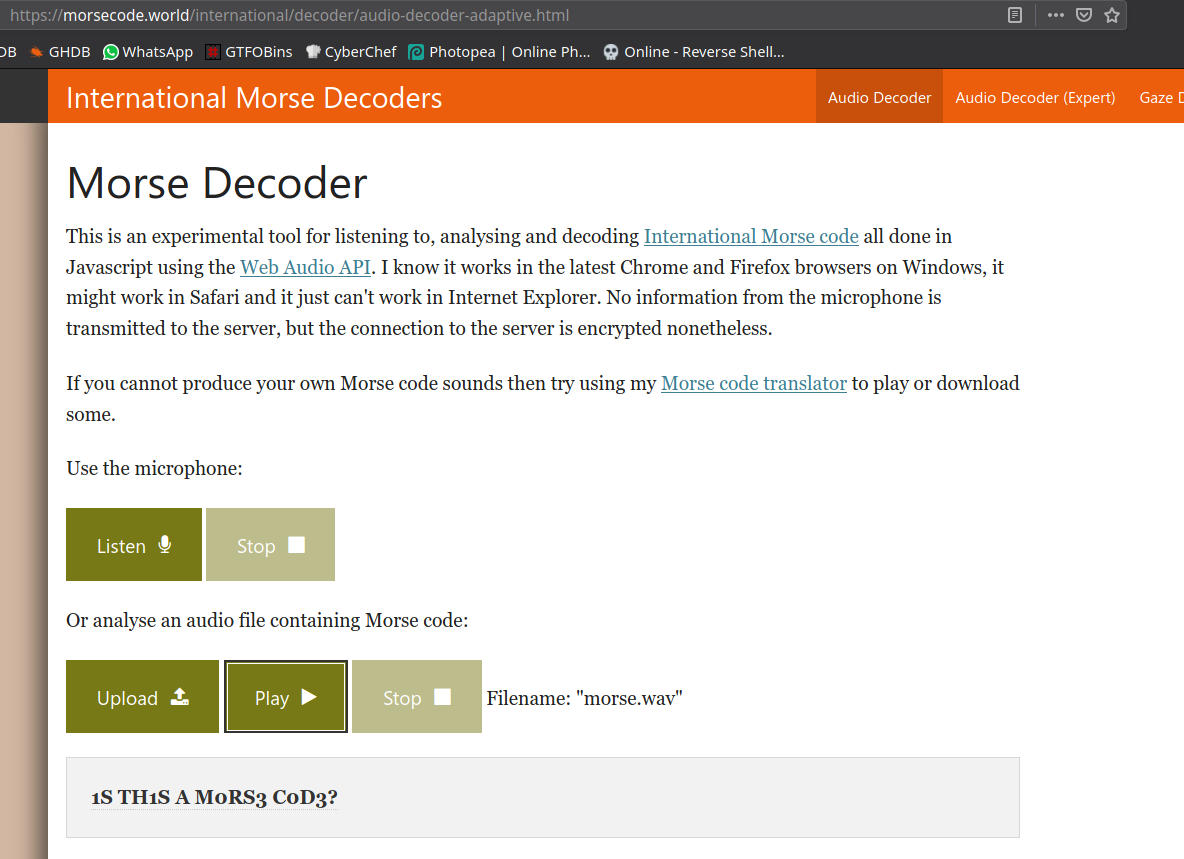
It’s a Morse Code audio, We can use Morse Decoder to get the flag, Upload and play the audio. The decrypted message will be our flag.
1
gravithon{1S TH1S A M0RS3 C0D3?}
Fly High to Tianjin
Challenge:
1
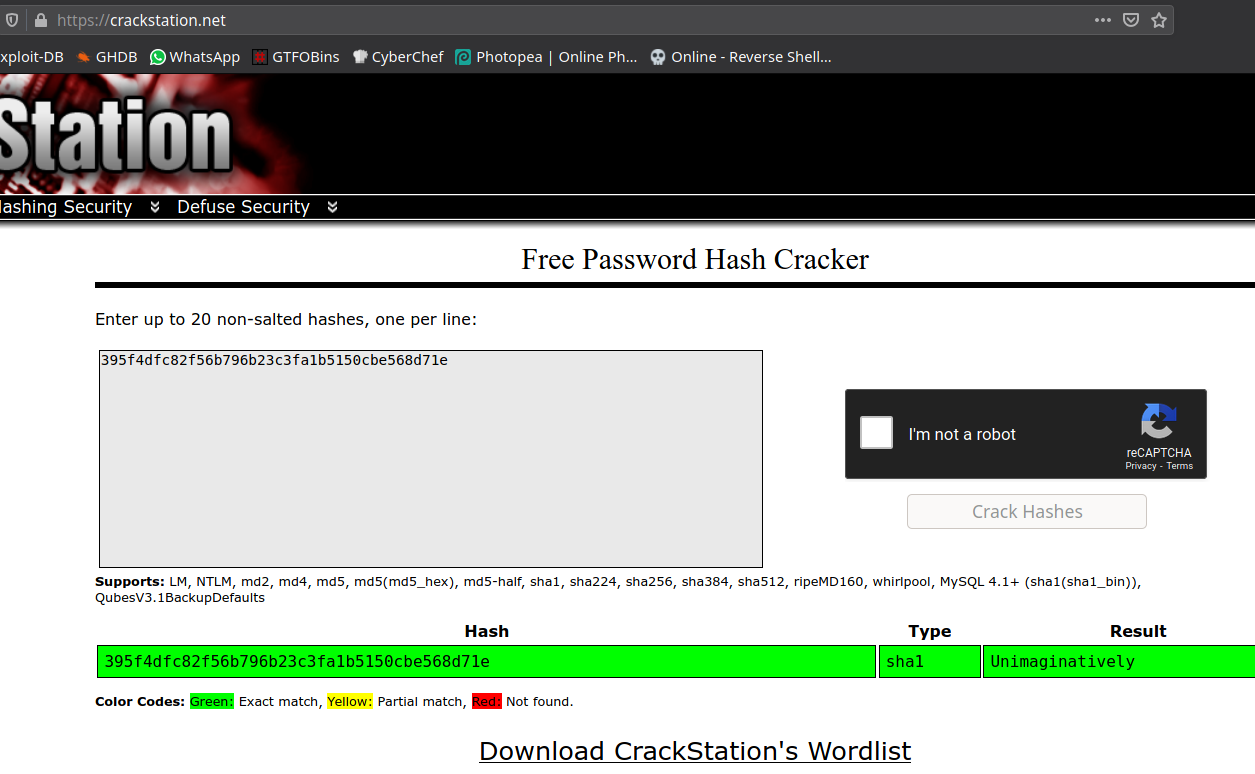
395f4dfc82f56b796b23c3fa1b5150cbe568d71e
It’s a SHA1 hashing algorithm. I used CrackStation to crack the hash.
1
gravithon{Unimaginatively}
Medium
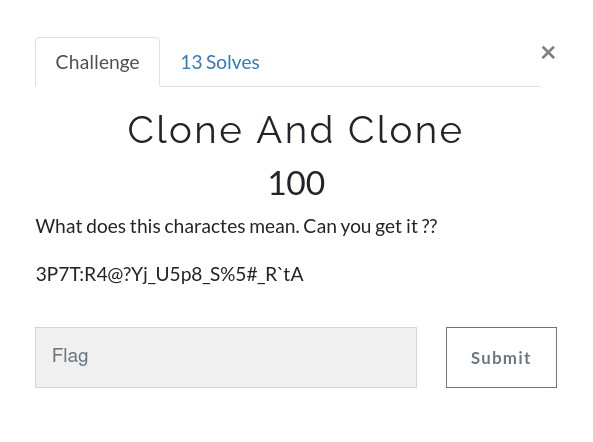
Clone And Clone
Challenge:
1
3P7T:R4@?Yj_U5p8_S%5#_R`tA
It looks like a ROT47 string, When we do ROT13 and ROT47 we, get our flag like this ` brfvitcon{H0wd4g0uTdR0t18} `.
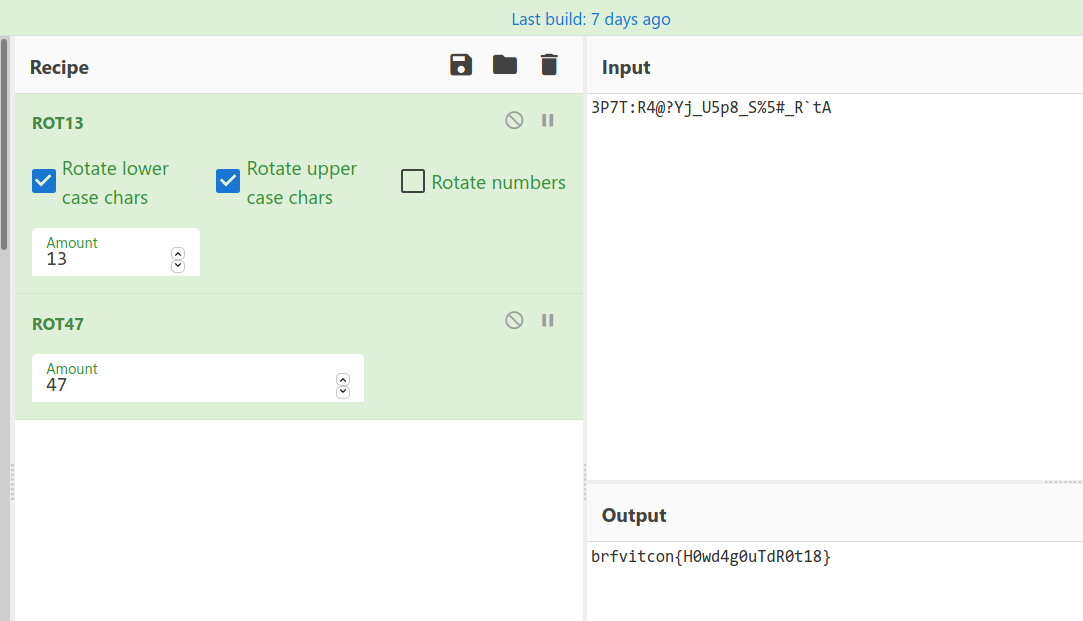
The flag has 3 words, first and last is set for us. what i done here guessed the middle word. that is H0w_4b0uT_R0t18
1
gravithon{H0w_4b0uT_R0t18}
Not that Tough

Challenge:
1
MFEFEMDDJBGTMTDZHEYGCVZVGVSFQSTTJRWU45TCKM4WWYRSGVWGIMTMGBQUOZDZLFMFU4DEI5UHMYTNGV3GKVZZGFMVQSTMMJWTSMA
It’s multiple encoded string, that is first Base32 then Base64, gives a shorted url https://tinyurl.com/donewithgravithonnoyouarenot

the link going for another encoded cipher that is Pikalang,
1
pi pi pi pi pi pi pi pi pi pi pika pipi pi pipi pi pi pi pipi pi pi pi pi pi pi pi pipi pi pi pi pi pi pi pi pi pi pi pichu pichu pichu pichu ka chu pipi pipi pipi ka ka ka ka ka pikachu pipi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pikachu pichu ka ka ka ka ka ka ka ka ka ka ka ka ka ka pikachu pipi ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka pikachu pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pikachu pichu ka ka ka pikachu pipi ka ka ka ka pikachu ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka pikachu pi pi pi pi pi pi pi pikachu pichu pi pi pi pi pikachu pipi pi pi pi pi pi pi pi pi pikachu ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka pikachu pichu ka ka ka ka pikachu pipi pi pi pi pi pi pi pi pikachu ka ka ka ka ka ka ka pikachu pichu pi pi pi pi pikachu pipi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pikachu pichu ka ka ka pikachu pipi ka pikachu pichu pi pi pikachu pipi ka ka ka ka ka ka ka ka ka ka ka ka ka ka pikachu pichu ka ka ka pikachu pipi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pikachu ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka pikachu ka ka ka ka ka ka ka ka ka ka ka ka ka ka ka pikachu pichu pi pikachu pipi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pi pikachu pichu pi pi pi pikachu pipi ka ka ka ka ka ka ka ka pikachu pi pi pi pi pi pikachu pi pi pi pi pi pi pi pi pi pi pi pi pi pikachu
Decode to get our flag.

1
gravithon{Ar3_y0u_f4n_0f_4n1m3_0r_P1k4chu}
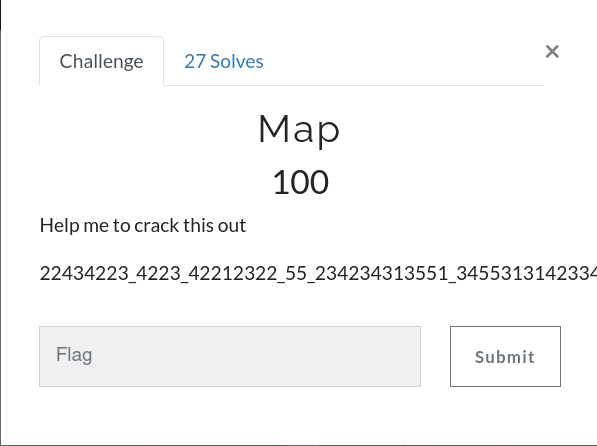
Map
Challenge:
1
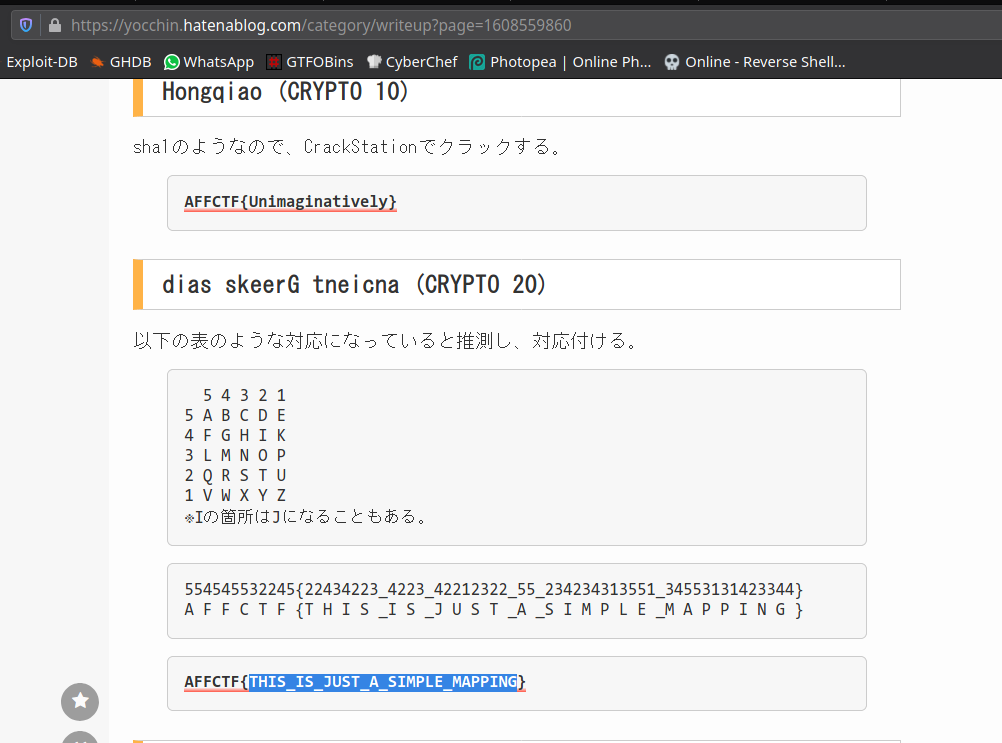
22434223_4223_42212322_55_234234313551_34553131423344
I just searched given string on google and found 3 results.
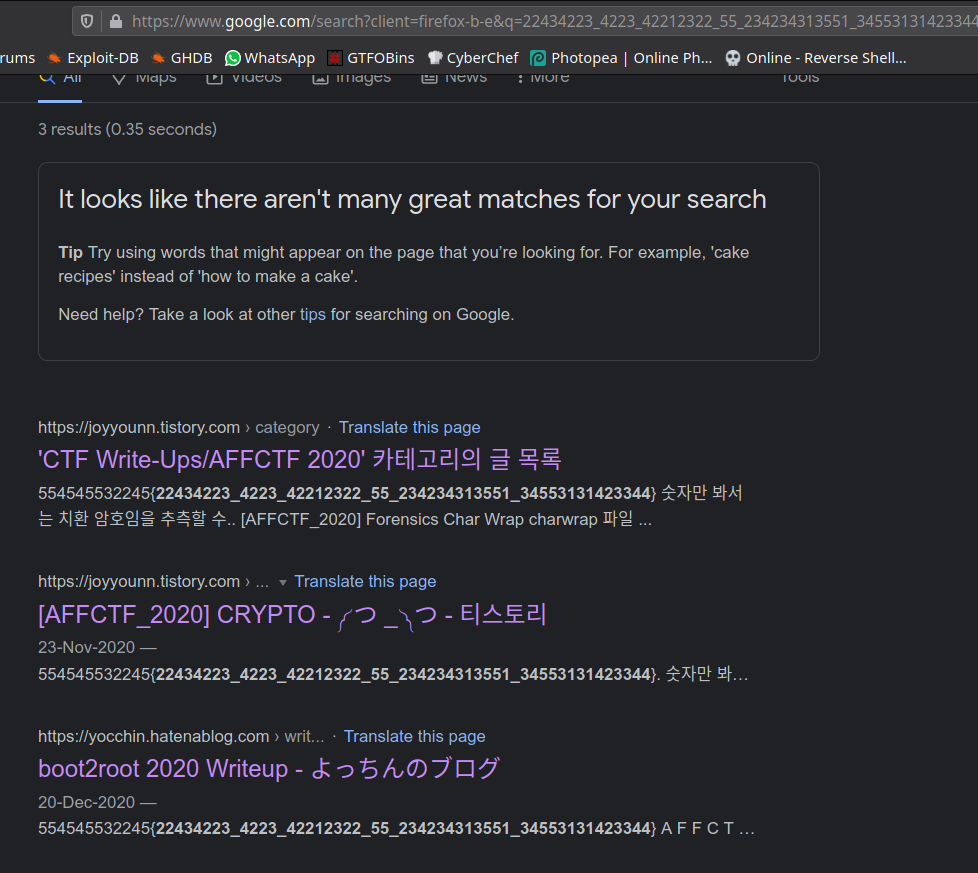
There is Japanese CTF writeups, from that we get our flag.
1
gravithon{THIS_IS_JUST_A_SIMPLE_MAPPING}
64 and 64
Challenge: 64Base64.txt
it’s a 38 times base64 encoded string, Decode to get your flag.
1
gravithon{l00ks_l1ke_4_l0t_0f_64s}
Rainbow Of Colors
Challenge: Rainbow_of_Colors.JPG

The challenge is about Hexahue Cipher. Decode and get your flag.
1
gravithon{should,fl5g4,b3,st1cky,or,n0t}
Hard
I lost my Way
Challenge: Who_am_I_.txt
It’s multiple encoded text file that is base32 and base64.
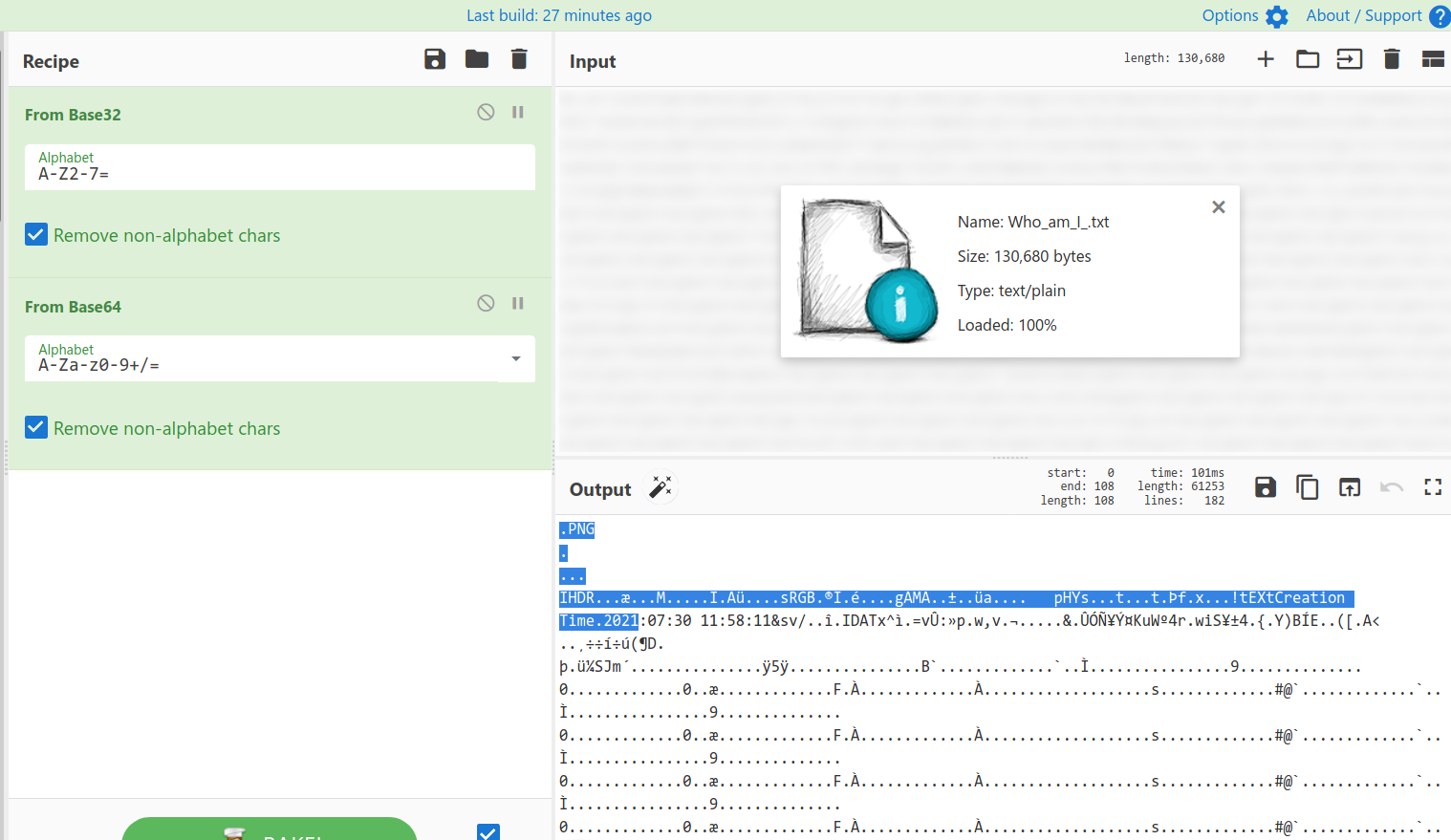
After that we will get PNG image file download it and open to get your flag. Wrap it in all Capital letters as per the instruction.
1
gravithon{F1N4LLY_Y0U_CR34T3D_B34UT1FUL_IM4G3}
Forensic
Look into it
Challenge: secret.jpeg
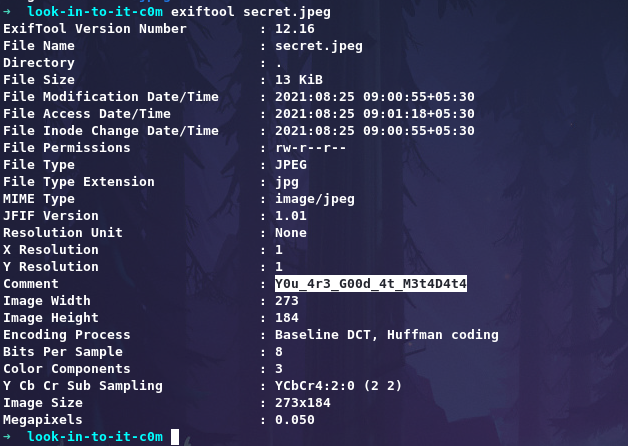
Use exiftool to get your flag.
1
exiftool secret.jpeg
1
gravithon{Y0u_4r3_G00d_4t_M3t4D4t4}
I can See You
Challenge: snow.zip
From the given file name snow.zip we know it’s a snow tool challenge. Here i used stegsnow to get the flag.
stegsnow is a program for concealing messages in text files by appending tabs and spaces on the end of lines, and for extracting messages from files containing hidden messages. Tabs and spaces are invisible to most text viewers, hence the steganographic nature of this encoding scheme.
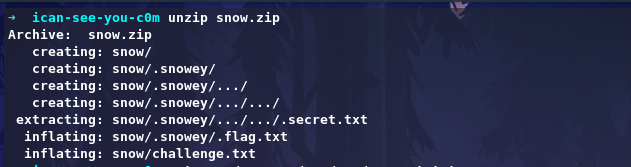
After extarcting the file we get 3 more files, There is a fake flag, and our challange, and passwd that is in .secret.txt
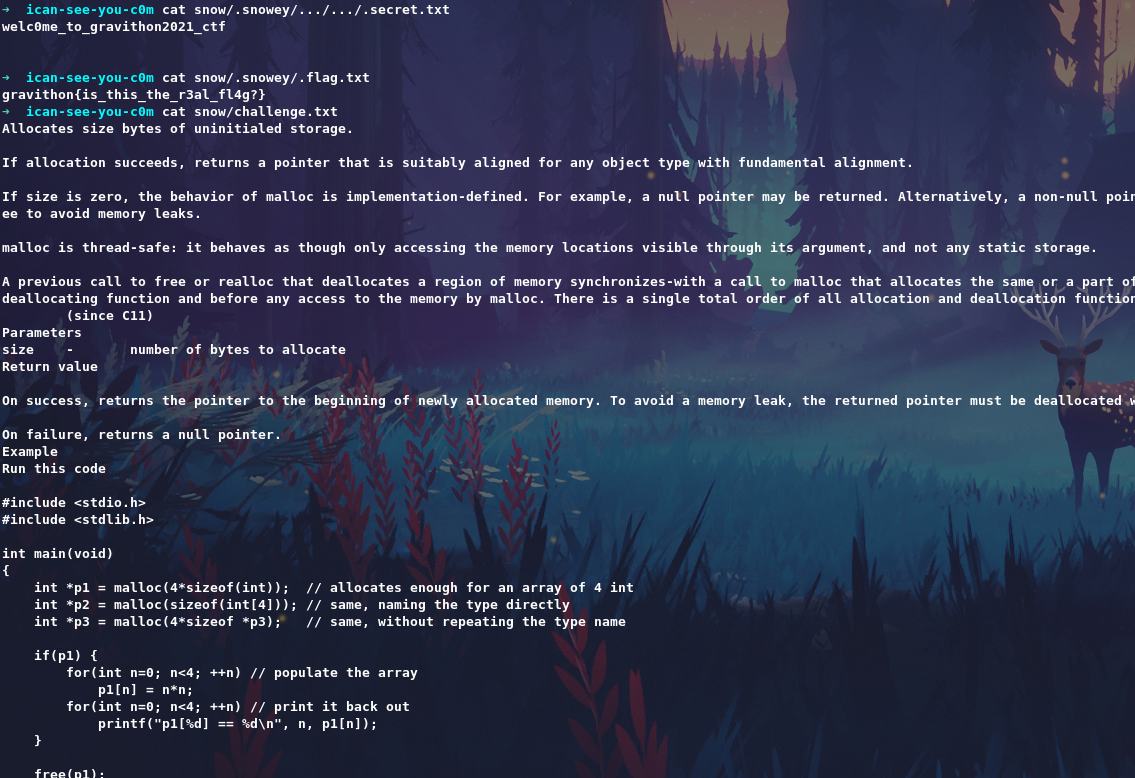
Use stegsnow to get the flag and give passwd as welc0me_to_gravithon2021_ctf from .secret.txt
1
2
stegsnow -C -Q -p welc0me_to_gravithon2021_ctf snow/challenge.txt
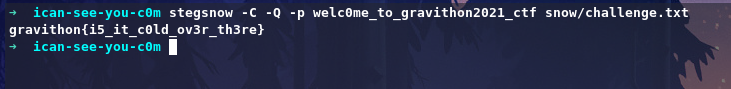
1
gravithon{i5_it_c0ld_ov3r_th3re}